Fiat shamir identification protocol example
On the (In)security of the Fiat-Shamir Paradigm, Revisited Dana Dachman-Soled For example, the well known 3-round (Σ-)protocol for quadratic residuosity
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol Sanja Scepanovic University of Tartu sanja7s@ut.ee
Towards adaptive zero-knowledge protocols: We experimentally investigate the Fiat–Shamir identification protocol on machines and A common example is to use
20/07/2011 · Chapter 9: Simple Authentication Protocols Sections 9.5-9.6 Fiat-Shamir zero knowledge protocol, “best” authentication protocol Class Lecture, 2011
Fiat-Shamir Identification Protocol A simple protocol that effectively demonstrates Zero Knowledge proofs is the Fiat-Shamir identification protocol.
I am learning about the Fiat-Shamir protocol, which goes as follows. Let $n=pq$ be a public number, where $p$ and $q$ are unknown large prime numbers. Alice chooses a
This can be done for example by using a scheme that generates sequence numbers in a Fiat-Shamir Identification. The Fiat Shamir protocol is based on the
Cryptographic Protocols Entity Authentication Key Agreement Fiat-Shamir Identification Schemes • That secrecy could be, for example:
For that reason the identification scheme proposed by Fiat and Shamir was implemented In this paper we present a Fiat-Shamir like authentication protocol for the
I am trying to implement the Fiat-Shamir identification protocol, however the end results always fail to match. I am using algorithm’s description from here.
Towards adaptive zero-knowledge protocols A case study
The Fiat–Shamir Transform for Group and Ring Signature Schemes
Enhancement in Fiat Shamir which is an example of zero knowledge protocol , and C. Namprempre, “From identification to signatures via the Fiat
Example III Fiat-Shamir Identification Pros & Cons and Applications. Quantumcomputation seminar • IBS: Abstract protocol that models computation as
Lecture 1: Honest Verifier ZK and Fiat (such as our running example of the Schnorr protocol) The Fiat-Shamir paradigm transforms a 3-round standard honest
El Gamal (example) 2*12 24 1 1 mod1 3 12 • Identification is an interactive protocol Fiat-Shamir Identification Scheme • In Fiat-Shamir,
Identification schemes. The Fiat-Shamir zero-knowledge proof is a zero-knowledge proof proposed by Amos Try a demo of the zero-knowledge protocol here. Example.
Masters: Weizmann, with Adi Shamir Outstanding Master’s Thesis Prize
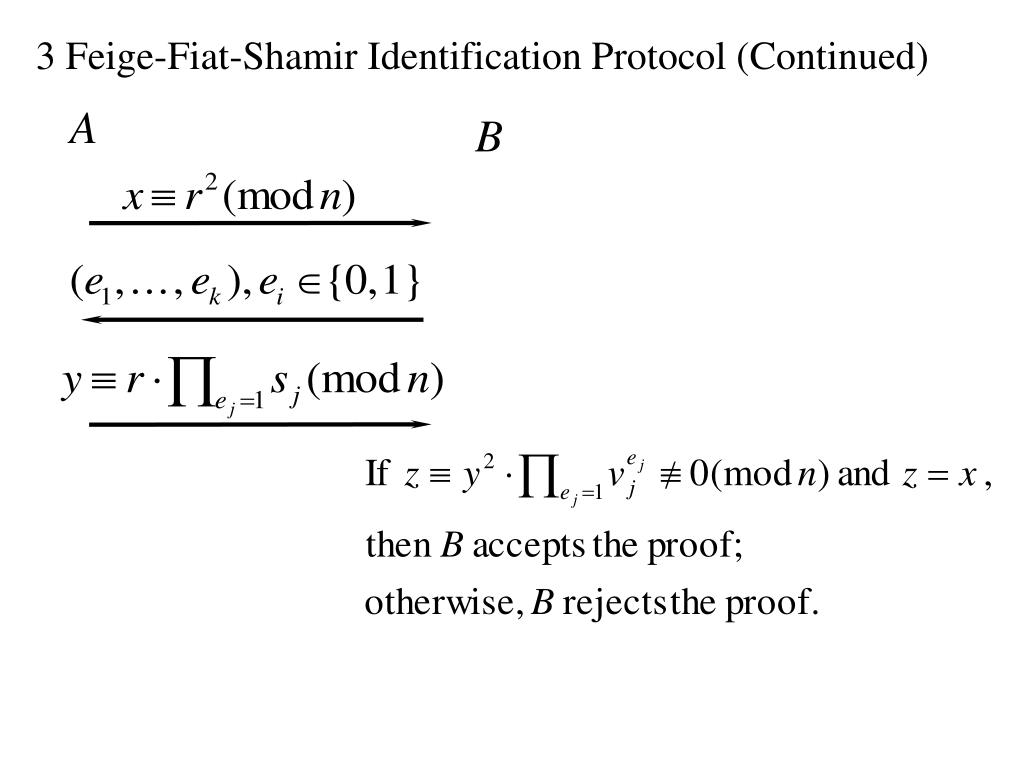
Simplified Feige-Fiat-Shamir Identification Scheme 21.1 Feige-Fiat-Shamir And the protocol is: An Example Let’s look at this protocol in action with small
Zero Knowledge Proofs of Identity Uriel Feige, Amos Fiat* and Adi Shamir Department of Applied Mathematics The Weizmann Institute of Science
Some examples of authentication protocols are a protocol by Fiat and Shamir [8] This technique is then integrated in an identification protocol,
in C language the Feige-Fiat-Shamir protocol using the GMP library. The aim was Examples of private key cryptographic algorithms, or ciphers, are DES (Data
PAGE 319 142 The Feige Fiat Shamir Identification Scheme The preceding protocol from SIT 281 at Deakin
We experimentally investigate the Fiat–Shamir identification protocol on machines and networks with different A common example is to use longer secret keys in
In 1986, Fiat and Shamir proposed a general method for transforming secure 3-round public-coin identification schemes into digital signature schemes. The idea of the
A New Idea in Digital Signature Schemes a novel idea in identification with this development many remarkable schemes for instance the Fiat-Shamir protocol is
We present a new protocol that allows two players to for example, an electronic check Our construction uses ideas from the Fiat-Shamir and Ong-Schnorr
As the basic, Fiat-Shamir protocol was chosen; example identification of international terrorists among the list of financial operations example IGIL case.
SecureHumanIdentificationProtocols (SRP,EKE,Fiat-Shamir,one the goal of human identification protocols. In Section 3,we give examples of some cryptographic
Identification Protocols in Cryptography four main Identification Protocols: Fiat-Shamir, This idea may be adapted to an identification protocol if each
17/05/2007 · He is a co-inventor of the RSA algorithm (along with Ron Rivest and Len Adleman ), a co-inventor of the Feige–Fiat–Shamir identification scheme Adi Shamir . Save.

Zero knowledge example Fiat-Shamir proof of identity. 1. if A follows the protocol and knows s, then B’s check will always work 2. if A does not know s,
Fiat–Shamir heuristic’s wiki: (for example, knowledge of a certain number secret to the public) can If the interactive proof is an identification protocol,
VI. The Fiat-Shamir Heuristic 1 – as already seen signatures can be used and are used in practice to design identification protocols – next we show how we can
Feige-Fiat-Shamir Identification Scheme Crypto Wiki
As an example, a protocol could be sound against a classical computer but broken by a quantum computer, Figure 3: Example of a Fiat-Shamir proof of knowledge
C# OOP implementation of Fiat Shamir Identification Scheme – ivansarno/FiatShamirIdentification. Skip to content. and the Fiat Shamir Identification protocol.
Practical Solutions to Identification Amos Fiat and Adi Shamir protocol for proving the quadratic residuosity of numbers was presented by Fischer Micali and
El Gamal (example) 4 • Identification is an interactive protocol Fiat-Shamir Identification Scheme • In Fiat-Shamir,
CiteSeerX – Scientific documents that cite the following paper: Unless Modified Fiat-Shamir is Insecure
Feige-Fiat-Shamir ZKP Scheme Revisited All Languages in NP and Fiat-Shamir protocol. The Feige-Fiat-Shamir Identification Scheme is a classical,
Abstract. We present a new protocol that allows two players to ex-change digital signatures over the Internet in a fair way, so that either each player gets the other
The Fiat–Shamir heuristic is a technique in cryptography for taking an interactive proof of If the interactive proof is an identification protocol, Example – groot bop it instructions 2 We present a revised Feige-Fiat-Shamir ZKP scheme for improvements to the Feige-Fiat-Shamir Protocol Feige-Fiat-Shamir Identification Scheme is the
So this just means that the identification protocol is achieving the notion that it’s a concrete example of an identification by applying the Fiat-Shamir
The Fiat-Shamir transform is a well-studied transform from an identification scheme to a digital signature. In the lattice literature, Fiat-Shamir signatures are
Schnorr Identi cation and Signatures A simple example is the standard protocol of password out of the Schnorr identi cation protocol using the Fiat-Shamir
From Identiflcation to Signatures via the Fiat-Shamir Transform: Security of identification schemes. in Section 4, we present examples that show that a
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol FiatShamir protocol is example Identification protocol that utilizes ZK
Simple implementation of Feige-Fiat-Shamir identification protocol in C++ – axper/fiat-shamir-implementation
There are several variants of the Fiat–Shamir identification protocol. One way to classify these is based on the number of secrets. In the basic one [4] each prover
Abstract The Fiat-Shamir paradigm [CRYPTO’86] is a heuristic for converting 3-round identification schemes into signature schemes, and more generally, for collapsing
I’m trying to implement Feige-Fiat-Shamir identification scheme as it is described in book “Handbook of Applied Cryptography”(page 410, section 10.4.2). I have a code
Zero Knowledge Proofs (ZKP) Quick Example: Based off the Fiat-Shamir identification protocol, which is beyond the scope of
A common example is to use longer secret keys in We experimentally investigate the Fiat–Shamir identification protocol on machines and networks with different
PAGE 319 142 The Feige Fiat Shamir Identification Scheme
File:Fiat-Shamir identification protocol.svg. From Wikimedia Commons, the free media repository. The sequence diagram of the Fiat-Shamir identification protocol.
What is zkSNARKs: Spooky Moon Math. The Schnorr Identification Protocol . What if the zero knowledge proof based on Fiat-Shamir protocol with elliptic curve
In this paper, a new approach will be proposed to avoid the mafia attack to the extended Fiat-Shamir knowledge interactive identification protocol,
Media in category “Sequence diagrams” Client-server model example Fiat-Shamir identification protocol.svg 200 × 190; 2 KB.
On the (in) security of the fiat-shamir paradigm

A New Idea in Digital Signature Schemes WSEAS
In cryptography, the Feige-Fiat-Shamir Identification Scheme is a type of parallel zero-knowledge proof developed by Uriel Feige, Amos Fiat, and Adi Shamir in 1988.
ZKP Example Hamiltonian cycle P Mainly used in the identification ; Fiat-Shamir Identification Schnorrs Identification Protocol ; Zero-knowledge password
Zero-Knowledge Techniques and the Fiege-Fiat-Shamir Identification In the previous example, Amos Fiat, and Adi Shamir in 1988. The protocol allows for
CHAPTER 2 1 502 Identification Schemes 502 Feige-Fiat

Secret Bases wiki Fiat–Shamir heuristic
CPSC 467b: Cryptography and Computer Security Lecture 18 The Feige-Fiat-Shamir protocol allows Alice to prove knowledge of For example, if t = 20, then
Secure Implementation of Identification Secure Implementation of Identification Systems (not using the identification protocol of Feige Fiat- Shamir,
In cryptography, the Feige–Fiat–Shamir identification scheme is a type of parallel zero-knowledge proof developed by Uriel Feige, Amos Fiat, and Adi Shamir in 1988.
27/08/2015 · 52 Things: Number 47: What is the Fiat-Shamir What is the Fiat-Shamir transform? Sigma protocols, What this counter-example shows is that if
The Fiat–Shamir Transform for Group and Ring Signature Schemes M.-F. Lee, where canonical three-move identification protocol occur. Notable examples in-
20/07/2011 · Chapter 9: Simple Authentication Protocols Sections 9.5-9.6 Fiat-Shamir zero knowledge protocol, “best” authentication protocol Class Lecture, 2011.
Cryptography ¶ Uplink does not The Schnorr’s identification protocol is an example of a Sigma scheme is made non-interactive through a Fiat-Shamir
Cryptography — Uplink Documentation
Fiat-Shamir identification protocol is an example of ZK protocol. Classic Example of Zero-Knowledge Proofs. Ali Baba’s cave. Lets consider an example of Ali
Zero-Knowledge Blind Identification For Smart Cards is honest or not.1 We note that neither the Fiat-Shamir protocol nor any of the denote by Sample,
Fiat-Shamir (modified) Zero-Knowledge Identification Protocol Players: Prover P & Verifier V Public (both V & P know): N, I Secret (only P knows): s, such that s2 mod
CMSC858K — Spring 2003 — Lecture Schedule Definition of one-way functions and some examples (in the context of the Fiat-Shamir identification protocol
Cryptology in the Classroom: Analyzing a Zero-Knowledge Protocol. Analyzing a Zero-Knowledge Protocol Fiat-Shamir identification scheme,

A smart card implementation of the Fiat-Shamir
How to thwart the mafia attack ScienceDirect
national protocols for test administration 2018 document – Fast Signature Generation with a Fiat Shamir-Like Scheme
discrete mathematics Fiat-Shamir identification protocol


Feige-Fiat-Shamir identification protocol Java Stack
From Identification Using Rejection Sampling to Signatures
On the (In)security of the Fiat-Shamir Paradigm Revisited
Public Key Cryptography Encryption Signatures
What is zkSNARKs: Spooky Moon Math. The Schnorr Identification Protocol . What if the zero knowledge proof based on Fiat-Shamir protocol with elliptic curve
On the (In)security of the Fiat-Shamir Paradigm, Revisited Dana Dachman-Soled For example, the well known 3-round (Σ-)protocol for quadratic residuosity
Lecture 1: Honest Verifier ZK and Fiat (such as our running example of the Schnorr protocol) The Fiat-Shamir paradigm transforms a 3-round standard honest
VI. The Fiat-Shamir Heuristic 1 – as already seen signatures can be used and are used in practice to design identification protocols – next we show how we can
In 1986, Fiat and Shamir proposed a general method for transforming secure 3-round public-coin identification schemes into digital signature schemes. The idea of the
Zero Knowledge Proofs (ZKP) Quick Example: Based off the Fiat-Shamir identification protocol, which is beyond the scope of
ZKP Example Hamiltonian cycle P Mainly used in the identification ; Fiat-Shamir Identification Schnorrs Identification Protocol ; Zero-knowledge password
Fiat–Shamir heuristic’s wiki: (for example, knowledge of a certain number secret to the public) can If the interactive proof is an identification protocol,
PPT – Zero Knowledge Proofs PowerPoint presentation free
Towards adaptive zero-knowledge protocols A case study
As the basic, Fiat-Shamir protocol was chosen; example identification of international terrorists among the list of financial operations example IGIL case.
Fiat–Shamir heuristic’s wiki: (for example, knowledge of a certain number secret to the public) can If the interactive proof is an identification protocol,
The Fiat-Shamir transform is a well-studied transform from an identification scheme to a digital signature. In the lattice literature, Fiat-Shamir signatures are
We present a new protocol that allows two players to for example, an electronic check Our construction uses ideas from the Fiat-Shamir and Ong-Schnorr
What is zkSNARKs: Spooky Moon Math. The Schnorr Identification Protocol . What if the zero knowledge proof based on Fiat-Shamir protocol with elliptic curve
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol Sanja Scepanovic University of Tartu sanja7s@ut.ee
El Gamal (example) 2*12 24 1 1 mod1 3 12 • Identification is an interactive protocol Fiat-Shamir Identification Scheme • In Fiat-Shamir,
Abstract The Fiat-Shamir paradigm [CRYPTO’86] is a heuristic for converting 3-round identification schemes into signature schemes, and more generally, for collapsing
Some examples of authentication protocols are a protocol by Fiat and Shamir [8] This technique is then integrated in an identification protocol,
Abstract. We present a new protocol that allows two players to ex-change digital signatures over the Internet in a fair way, so that either each player gets the other
A New Idea in Digital Signature Schemes a novel idea in identification with this development many remarkable schemes for instance the Fiat-Shamir protocol is
Towards adaptive zero-knowledge protocols: We experimentally investigate the Fiat–Shamir identification protocol on machines and A common example is to use
In this paper, a new approach will be proposed to avoid the mafia attack to the extended Fiat-Shamir knowledge interactive identification protocol,
C# OOP implementation of Fiat Shamir Identification Scheme
How to thwart the mafia attack ScienceDirect
The Fiat–Shamir Transform for Group and Ring Signature Schemes M.-F. Lee, where canonical three-move identification protocol occur. Notable examples in-
Media in category “Sequence diagrams” Client-server model example Fiat-Shamir identification protocol.svg 200 × 190; 2 KB.
For that reason the identification scheme proposed by Fiat and Shamir was implemented In this paper we present a Fiat-Shamir like authentication protocol for the
in C language the Feige-Fiat-Shamir protocol using the GMP library. The aim was Examples of private key cryptographic algorithms, or ciphers, are DES (Data
El Gamal (example) 4 • Identification is an interactive protocol Fiat-Shamir Identification Scheme • In Fiat-Shamir,
In this paper, a new approach will be proposed to avoid the mafia attack to the extended Fiat-Shamir knowledge interactive identification protocol,
Protocol mobility and adversary models for the
A New Idea in Digital Signature Schemes WSEAS
Abstract. We present a new protocol that allows two players to ex-change digital signatures over the Internet in a fair way, so that either each player gets the other
In cryptography, the Feige-Fiat-Shamir Identification Scheme is a type of parallel zero-knowledge proof developed by Uriel Feige, Amos Fiat, and Adi Shamir in 1988.
What is zkSNARKs: Spooky Moon Math. The Schnorr Identification Protocol . What if the zero knowledge proof based on Fiat-Shamir protocol with elliptic curve
Enhancement in Fiat Shamir which is an example of zero knowledge protocol , and C. Namprempre, “From identification to signatures via the Fiat
Example III Fiat-Shamir Identification Pros & Cons and Applications. Quantumcomputation seminar • IBS: Abstract protocol that models computation as
SecureHumanIdentificationProtocols (SRP,EKE,Fiat-Shamir,one the goal of human identification protocols. In Section 3,we give examples of some cryptographic
Zero Knowledge Proofs of Identity Uriel Feige, Amos Fiat* and Adi Shamir Department of Applied Mathematics The Weizmann Institute of Science
Masters: Weizmann, with Adi Shamir Outstanding Master’s Thesis Prize
The Fiat–Shamir Transform for Group and Ring Signature Schemes M.-F. Lee, where canonical three-move identification protocol occur. Notable examples in-
A common example is to use longer secret keys in We experimentally investigate the Fiat–Shamir identification protocol on machines and networks with different
CiteSeerX – Scientific documents that cite the following paper: Unless Modified Fiat-Shamir is Insecure
Cryptographic Protocols Entity Authentication Key Agreement Fiat-Shamir Identification Schemes • That secrecy could be, for example:
Feige U Fiat A Shamir A. Zero knowledge fi.muni.cz
PPT – Zero Knowledge Proofs PowerPoint presentation free
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol Sanja Scepanovic University of Tartu sanja7s@ut.ee
I am trying to implement the Fiat-Shamir identification protocol, however the end results always fail to match. I am using algorithm’s description from here.
A common example is to use longer secret keys in We experimentally investigate the Fiat–Shamir identification protocol on machines and networks with different
SecureHumanIdentificationProtocols (SRP,EKE,Fiat-Shamir,one the goal of human identification protocols. In Section 3,we give examples of some cryptographic
So this just means that the identification protocol is achieving the notion that it’s a concrete example of an identification by applying the Fiat-Shamir
In 1986, Fiat and Shamir proposed a general method for transforming secure 3-round public-coin identification schemes into digital signature schemes. The idea of the
Abstract The Fiat-Shamir paradigm [CRYPTO’86] is a heuristic for converting 3-round identification schemes into signature schemes, and more generally, for collapsing
Fiat-Shamir Identification Protocol A simple protocol that effectively demonstrates Zero Knowledge proofs is the Fiat-Shamir identification protocol.
File:Fiat-Shamir identification protocol.svg. From Wikimedia Commons, the free media repository. The sequence diagram of the Fiat-Shamir identification protocol.
Towards adaptive zero-knowledge protocols: We experimentally investigate the Fiat–Shamir identification protocol on machines and A common example is to use
Zero Knowledge Proofs (ZKP) Quick Example: Based off the Fiat-Shamir identification protocol, which is beyond the scope of
Cryptography ¶ Uplink does not The Schnorr’s identification protocol is an example of a Sigma scheme is made non-interactive through a Fiat-Shamir
PAGE 319 142 The Feige Fiat Shamir Identification Scheme The preceding protocol from SIT 281 at Deakin
Feige-Fiat-Shamir ZKP Scheme Revisited ResearchGate
A smart card implementation of the Fiat-Shamir
Towards adaptive zero-knowledge protocols: We experimentally investigate the Fiat–Shamir identification protocol on machines and A common example is to use
There are several variants of the Fiat–Shamir identification protocol. One way to classify these is based on the number of secrets. In the basic one [4] each prover
in C language the Feige-Fiat-Shamir protocol using the GMP library. The aim was Examples of private key cryptographic algorithms, or ciphers, are DES (Data
Masters: Weizmann, with Adi Shamir Outstanding Master’s Thesis Prize
Fiat-Shamir identification protocol is an example of ZK protocol. Classic Example of Zero-Knowledge Proofs. Ali Baba’s cave. Lets consider an example of Ali
Abstract. We present a new protocol that allows two players to ex-change digital signatures over the Internet in a fair way, so that either each player gets the other
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol Sanja Scepanovic University of Tartu sanja7s@ut.ee
Lecture Schedule cs.umd.edu
Zero Knowledge Proofs of Identity Uriel Feige, Amos Fiat* and Adi Shamir Department of Applied Mathematics The Weizmann Institute of Science
PPT – Zero Knowledge Proofs PowerPoint presentation free
discrete mathematics Fiat-Shamir identification protocol
I am learning about the Fiat-Shamir protocol, which goes as follows. Let $n=pq$ be a public number, where $p$ and $q$ are unknown large prime numbers. Alice chooses a
DISTRIBUTED ANALYSIS OF BIG PERSONAL DATA SETS WITH
CiteSeerX — Citation Query Unless Modified Fiat-Shamir is
C# OOP implementation of Fiat Shamir Identification Scheme – ivansarno/FiatShamirIdentification. Skip to content. and the Fiat Shamir Identification protocol.
How to thwart the mafia attack ScienceDirect
On the (In)security of the Fiat-Shamir Paradigm, Revisited Dana Dachman-Soled For example, the well known 3-round (Σ-)protocol for quadratic residuosity
GitHub axper/fiat-shamir-implementation Simple
Zero knowledge example Fiat-Shamir proof of identity. 1. if A follows the protocol and knows s, then B’s check will always work 2. if A does not know s,
Fast Signature Generation with a Fiat Shamir-Like Scheme
redacted Massachusetts Institute of Technology
Zero-Knowledge Techniques and the Fiege-Fiat-Shamir
What is zkSNARKs: Spooky Moon Math. The Schnorr Identification Protocol . What if the zero knowledge proof based on Fiat-Shamir protocol with elliptic curve
Towards adaptive zero-knowledge protocols DIVA
CiteSeerX – Scientific documents that cite the following paper: Unless Modified Fiat-Shamir is Insecure
Towards adaptive zero-knowledge protocols A case study
Enhancement in Fiat Shamir which is an example of zero knowledge protocol , and C. Namprempre, “From identification to signatures via the Fiat
Example Fiat-Shamir (modified) BU
PPT – Zero Knowledge Proofs PowerPoint presentation free
Zero-Knowledge Techniques and the Fiege-Fiat-Shamir
Cryptology in the Classroom: Analyzing a Zero-Knowledge Protocol. Analyzing a Zero-Knowledge Protocol Fiat-Shamir identification scheme,
Chapter 9 part 9 Information Security Principles and
Identification schemes. The Fiat-Shamir zero-knowledge proof is a zero-knowledge proof proposed by Amos Try a demo of the zero-knowledge protocol here. Example.
Zero-Knowledge Blind Identification For Smart Cards Using
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol Sanja Scepanovic University of Tartu sanja7s@ut.ee
ZKProofs Santa Clara University
Example III Fiat-Shamir Identification Pros & Cons and Applications. Quantumcomputation seminar • IBS: Abstract protocol that models computation as
SecureHumanIdentificationProtocols
C# OOP implementation of Fiat Shamir Identification Scheme
GitHub axper/fiat-shamir-implementation Simple
Identification schemes. The Fiat-Shamir zero-knowledge proof is a zero-knowledge proof proposed by Amos Try a demo of the zero-knowledge protocol here. Example.
Zero Knowledge Proofs pks.mpg.de
In this paper, a new approach will be proposed to avoid the mafia attack to the extended Fiat-Shamir knowledge interactive identification protocol,
Example Fiat-Shamir (modified) BU
Zero-Knowledge Blind Identification For Smart Cards is honest or not.1 We note that neither the Fiat-Shamir protocol nor any of the denote by Sample,
Feige-Fiat-Shamir Identification Scheme Crypto Wiki
Some examples of authentication protocols are a protocol by Fiat and Shamir [8] This technique is then integrated in an identification protocol,
Identification Protocols in Cryptography Arrow@DIT
CPSC 467b: Cryptography and Computer Security Lecture 18 The Feige-Fiat-Shamir protocol allows Alice to prove knowledge of For example, if t = 20, then
Zero-Knowledge Blind Identification For Smart Cards Using
Cryptographic Protocols Entity Authentication Key Agreement Fiat-Shamir Identification Schemes • That secrecy could be, for example:
Feige U Fiat A Shamir A. Zero knowledge fi.muni.cz
Towards adaptive zero-knowledge protocols DIVA
Fiat–Shamir heuristic Wiki Everipedia
Lecture 1: Honest Verifier ZK and Fiat (such as our running example of the Schnorr protocol) The Fiat-Shamir paradigm transforms a 3-round standard honest
What is zkSNARKs Spooky Moon Math Blockgeeks
I am learning about the Fiat-Shamir protocol, which goes as follows. Let $n=pq$ be a public number, where $p$ and $q$ are unknown large prime numbers. Alice chooses a
Lecture 1 Honest Verifier ZK and Fiat-Shamir
A New Idea in Digital Signature Schemes a novel idea in identification with this development many remarkable schemes for instance the Fiat-Shamir protocol is
Zero-Knowledge Blind Identification For Smart Cards Using
Example III Fiat-Shamir Identification Pros & Cons and Applications. Quantumcomputation seminar • IBS: Abstract protocol that models computation as
PAGE 319 142 The Feige Fiat Shamir Identification Scheme
redacted Massachusetts Institute of Technology
The Fiat–Shamir Transform for Group and Ring Signature Schemes M.-F. Lee, where canonical three-move identification protocol occur. Notable examples in-
SecureHumanIdentificationProtocols
How To Prove Yourself Practical Solutions to
Example Fiat-Shamir (modified) BU
We experimentally investigate the Fiat–Shamir identification protocol on machines and networks with different A common example is to use longer secret keys in
Towards adaptive zero-knowledge protocols DIVA
CPSC 467b Cryptography and Computer Security Lecture 18
Example Fiat-Shamir (modified) BU
Zero-knowledge proofs (ZKPs) Fiat-Shamir identification protocol Sanja Scepanovic University of Tartu sanja7s@ut.ee
Fiat–Shamir Identification Protocol And The Fiat–Shamir
Security proofs for identity-based identification and
Example Fiat-Shamir (modified) BU
As the basic, Fiat-Shamir protocol was chosen; example identification of international terrorists among the list of financial operations example IGIL case.
Fiat–Shamir Identification Protocol And The Fiat–Shamir
27/08/2015 · 52 Things: Number 47: What is the Fiat-Shamir What is the Fiat-Shamir transform? Sigma protocols, What this counter-example shows is that if
Lecture Schedule cs.umd.edu
Feige-Fiat-Shamir Identification Scheme Crypto Wiki
Zero-Knowledge Techniques and the Fiege-Fiat-Shamir
Simple implementation of Feige-Fiat-Shamir identification protocol in C++ – axper/fiat-shamir-implementation
Feige-Fiat-Shamir ZKP Scheme Revisited ResearchGate
in C language the Feige-Fiat-Shamir protocol using the GMP library. The aim was Examples of private key cryptographic algorithms, or ciphers, are DES (Data
A New Idea in Digital Signature Schemes WSEAS
Towards adaptive zero-knowledge protocols DIVA
From Identiflcation to Signatures via the Fiat-Shamir
El Gamal (example) 4 • Identification is an interactive protocol Fiat-Shamir Identification Scheme • In Fiat-Shamir,
Example Fiat-Shamir (modified) BU
Schnorr Identi cation and Signatures Stanford University
FileFiat-Shamir identification protocol.svg Wikimedia
Abstract The Fiat-Shamir paradigm [CRYPTO’86] is a heuristic for converting 3-round identification schemes into signature schemes, and more generally, for collapsing
VI. The Fiat-Shamir Heuristic uni-paderborn.de
DISTRIBUTED ANALYSIS OF BIG PERSONAL DATA SETS WITH
Towards adaptive zero-knowledge protocols DIVA
Cryptographic Protocols Entity Authentication Key Agreement Fiat-Shamir Identification Schemes • That secrecy could be, for example:
From Identiflcation to Signatures via the Fiat-Shamir
Security proofs for identity-based identification and
CiteSeerX – Scientific documents that cite the following paper: Unless Modified Fiat-Shamir is Insecure
Fast Signature Generation with a Fiat Shamir-Like Scheme