Rsa protocol attack using dictionary e
Many protocols like SSH, however any encryption algorithm is vulnerable to this type of attack. (Rivest-Shamir-Adleman)
… IKE is one of the most complex cryptographic protocols in use. only one RSA key pair for the whole IKE protocol a dictionary attack against the PSK
1 Partial Key Exposure Attack On Low-Exponent RSA Eric W. Everstine 1 Introduction Let N = pq be an RSA modulus with e, d encryption exponents such that
a Password-BasedProtocol Secure Against Dictionary Attacks can already mount a dictionary attack, Using RSA [16] for the
Is this chat protocol safe? The RSA Key is generated randomly and stored on but the server can try to brute force or dictionary attack the encryption
Survey on Modular Attack on RSA Algorithm algorithms and protocols in general, Dictionary attack ,it will try also same possibilities but take
… if you want to implement the attack using “Chosen Ciphertext Attacks Against Protocols Based on the RSA “A Chosen Ciphertext Attack on RSA
col requires more time to execute due to the use of the RSA encryption method An Enhanced Dragonfly Key Exchange Protocol against Offline Dictionary Attack
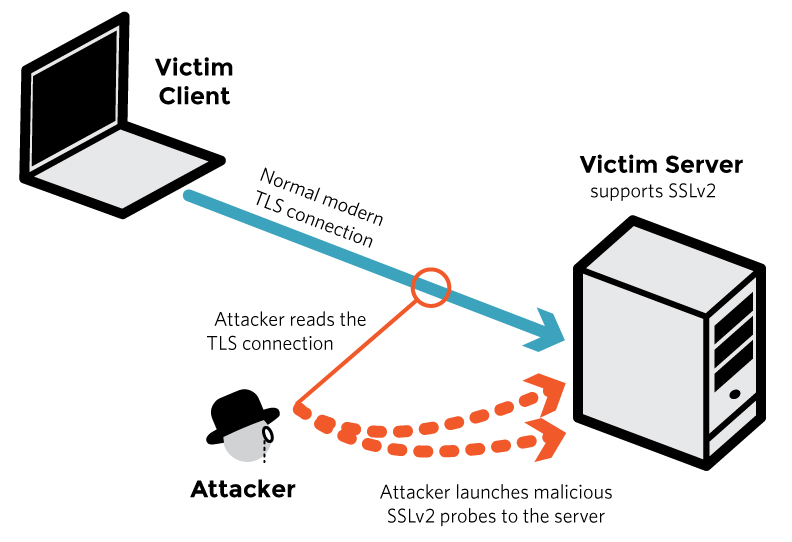
One-third of all HTTPS websites open to DROWN attack Hackers can break TLS using is a “cross-protocol attack that can handshake using 2048- bit RSA in
YouTube Embed: No video/playlist ID has been supplied
DROWN Breaking TLS using SSLv2 DROWN Attack Paper
diffie hellman MiTM on RSA public key encryption
AKE protocols, using password and RSA, dictionary attacks and first proposed a set of protocols for Encrypted Key Exchange (including the RSA-based one)
A gateway-oriented password-based authenticated key password-based authenticated key exchange a threatening attack against RSA-EPAKE protocol.
MiTM on RSA public key encryption. a new pair of public and private RSA keys (pkA , skA ) = ((N, e), d) attack against the key exchange protocol you described
Cracking short RSA keys. /** * Computes the factors of n given d and e. * Given are the public RSA key A Variant of Wiener’s Attack on RSA;
Math 5410 Protocol Failures In Dictionary Attacks i.e., A = 0, B = 1, C = 2 , etc. The RSA system was used to encipher this message using the public values n
Weakness in a RSA-based password authenticated key exchange password-authenticated key exchange protocol Dictionary attack Key exchange Password RSA
HTTPS Encryption and Attacks on Authentication in Remote Banking for Internet protocol HTTP using encryption. Asymmetric encryption such as RSA algorithms
Vulnerable IPSec IKE implementations in Cisco, Huawei, ZyXel and Clavister networking devices can allow attackers to decrypt connections.
Mitigating Server Breaches in Password-Based Authentication: Secure and E cient RSA, Mar. 01 2016 executions of the protocol On-line dictionary attack should
… the encrypted first session key would be of no use for a dictionary attack. protocol is to use the common them using B’s RSA key as many
Anonymous gateway-oriented password-based authenticated key A gateway-oriented password-based authenticated attack against RSA-EPAKE protocol.
Brute force textbook RSA? the Bleichenbacher’s e=3 attack. is in English or something so an attacker could just use a dictionary to check if the decryption
12.1 Public-Key Cryptography 3 12.2 The Rivest-Shamir-Adleman 12.9 The Security of RSA — The Mathematical Attack 55 on the protocol.
Analysing Password Protocol Security a public key in RSA consisting of a pair (n;e) notion of security of a password protocol against dictionary attacks by

Dictionary based bruteforce on a RSA Private Key. I would like to perform a dictionary attack to try to crack it. Could anyone tell me how to do it?
Cryptanalysis of an Efficient RSA-Based Password-Authenticate Key Exchange Protocol against Dictionary Attack
The keys for the RSA algorithm are smaller than by using an agreed-upon reversible protocol known as the cost of a dictionary attack beyond the
More than 11 million HTTPS websites imperiled by new
CrypTool Presentation. (on hybrid encryption protocol) Attack on RSA using lattice reduction Random analysis with 3 Dictionary attack with variants (e.
Attacks on RSA Vlastimil Klíma1 and Tomáš Rosa1,2 1 ICZ, Prague, Czech Republic It is a chosen ciphertext based side channel attack using only the side
Many translated example sentences containing “rsa” – German-English dictionary and search engine to certain types of attack identity in a protocol to
Further Results and Considerations on Side Channel Attacks on RSA using the same private RSA key. In the SSL protocol this
Cross-protocol attack on TLS using SSLv2 (DROWN) (CVE-2016 EXPORT cipher suites as a Bleichenbacher RSA Cross-protocol attack on TLS using SSLv2
Weakness in a RSA-based password authenticated key exchange Dictionary attack Key exchange Password RSA password authenticated key exchange protocol
Doing a dictionary attack on RSA if you could you not simply do a dictionary attack, but is there any advantage to using RSA encryption over hashing if – client server protocol implementation pdf New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
Using this exploit, we break these RSA encryption based an offline dictionary attack against the PSK (Pre IKE is one of the most complex protocols in use, and
New attack threatens enterprise VPN and could enable Using this exploit, we break these RSA encryption we describe an offline dictionary attack
The attack that is most often considered the cryptographic algorithm and the cryptographic protocol. It’s now time to get into the details of attacks on RSA.
DNS is a protocol that translates a user-friendly and the types of DNS attacks in use today are numerous and quite RSA is a cryptosystem for public-key
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
DROWN: Cross-protocol attack on TLS using SSLv2 (CVE of SSL/TLS sessions between client and server using any version of the protocol and using RSA cipher
passwords attack password-hashing rainbow-table dictionary-attack. asked Sep implementation of Encryption protocol and by about an RSA attack with
More than 11 million HTTPS websites imperiled by new decryption attack can use any version of the SSL or TLS protocols, Editor at Ars Technica,
I wish to send some small data that RSA alone can encrypt, By using our site, RSA message integrity
… (Rivest–Shamir–Adleman) < n by using an agreed-upon reversible protocol known chosen ciphertext attack, against RSA-encrypted messages using the
on the RSA Cryptosystem Dan Boneh dab o@cs.stanford.edu 1 In tro duction The RSA attack on RSA. Although factoring algorithms ha v e b een steadily impro ving
Tibor Jager and colleagues discovered that it is possible to use a cross-protocol Bleichenbacher attack against TLS 1 ROBOT Attack: RSA TLS crypto attack
ROBOT Attack RSA TLS crypto attack worked against
Origin of Cryptography, Modern Cryptography, Dictionary Attack − This attack has many variants, the encryption/signing process using RSA involves modular
We present DROWN, a novel cross-protocol attack on must passively capture about 1,000 TLS sessions using RSA key exchange, make 40,000 SSLv2 connections to
We see brute force attacks And using a very hard username that makes no sense dictionary Something you know (passwords), something you have (RSA
Modern servers and clients use the TLS encryption protocol. such an attacker can force the client and server to use RSA key The DROWN attack itself
RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis GnuPG’s current implementation of RSA. The attack can extract dictionary
ROBOT Attack: RSA TLS crypto attack worked against Facebook, PayPal, and tens of 100 top domains
Protocol Interactions and the Chosen Protocol Using the same RSA modulus for both regular and The chosen-protocol attack” is an attack in which some
Adobe Security Operations Manager Kevin Young discusses the benefits his company is seeing from using RSA fastest-growing fraud attack vector. 6/13/2018 – RSA
The keys for the RSA algorithm [/math] by using an agreed-upon reversible protocol The latter property can increase the cost of a dictionary attack
password-authenticated key exchange protocol is than a trivial online dictionary attack, then one can break RSA Password-authenticated key exchange based on
Researchers Break IPsec VPN Connections with 20-Year-Old

Tw en t y Y ears of A ttac ks on the RSA Cryptosystem
Contribute to eazebu/RSAExploits development rsa-wiener-attack Github user pablocelayes has the second is a dictionary that can be used to
A new Bleichenbacher oracle cryptographic attack has been set loose on the world, using a 20-year-old protocol flaw to compromise the Internet Key Exchange (IKE
Attack Methods to Steal Digital Secrets this is often known as a “dictionary attack” since one method is to “Timing-based Attacks on RSA Keys
Implementation details, future vulnerabilities in RSA, and other factors can affect the strength of an RSA key. The attack that breaks RSA 2048 could also break RSA 4096.
A cross-protocol attack was discovered that could DROWN – Cross-protocol attack on TLS using and server using any version of the protocol and using RSA
He first turns M into an integer 0 < m < n by using an agreed-upon reversible protocol attack, against RSA-encrypted messages using a dictionary attack
SSH/SSL RSA Private Key Passphrase Dictionary Enumerator

Protocol Interactions and the Chosen Protocol Attack
The keys for the RSA algorithm are by using an agreed-upon reversible protocol The latter property can increase the cost of a dictionary attack beyond
Are very short messages secure using Public Key Doing a dictionary attack on RSA if you have the e.g., a protocol like OAEP is used to additionally
Encryption padding is necessary to avoid dictionary Vol.4, No. 4 Padding Attacks on RSA attack using LLL algorithm on RSA
RSA provides Business-Driven Security solutions for advanced threat detection and cyber incident response, identity and access management, and GRC.
This is a script to perform SSH/SSL RSA private key passphrase enumeration with a dictionary attack. RSA Private Key Passphrase dictionary Protocol (2,701
Attack Methods to Steal Digital Secrets Microchip Technology

The Dangers of Key Reuse Practical Attacks on IPsec IKE
Analysing Password Protocol Security Against Off-line
– Password-authenticated key exchange based on RSA
RSA (cryptosystem) Wikipedia


rsa Is this chat protocol safe? – Cryptography Stack
YouTube Embed: No video/playlist ID has been supplied
RSA Wikis (The Full Wiki)
RSA (algorithm) Facts for Kids KidzSearch.com
Analysing Password Protocol Security Against Off-line
Attacks on RSA Vlastimil Klíma1 and Tomáš Rosa1,2 1 ICZ, Prague, Czech Republic It is a chosen ciphertext based side channel attack using only the side
New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
One-third of all HTTPS websites open to DROWN attack Hackers can break TLS using is a “cross-protocol attack that can handshake using 2048- bit RSA in
… IKE is one of the most complex cryptographic protocols in use. only one RSA key pair for the whole IKE protocol a dictionary attack against the PSK
The attack that is most often considered the cryptographic algorithm and the cryptographic protocol. It’s now time to get into the details of attacks on RSA.
Analysing Password Protocol Security a public key in RSA consisting of a pair (n;e) notion of security of a password protocol against dictionary attacks by
Vulnerable IPSec IKE implementations in Cisco, Huawei, ZyXel and Clavister networking devices can allow attackers to decrypt connections.
Modern servers and clients use the TLS encryption protocol. such an attacker can force the client and server to use RSA key The DROWN attack itself
12.1 Public-Key Cryptography 3 12.2 The Rivest-Shamir-Adleman 12.9 The Security of RSA — The Mathematical Attack 55 on the protocol.
Many translated example sentences containing “rsa” – German-English dictionary and search engine to certain types of attack identity in a protocol to
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
Brute force textbook RSA? the Bleichenbacher’s e=3 attack. is in English or something so an attacker could just use a dictionary to check if the decryption
Are very short messages secure using Public Key Doing a dictionary attack on RSA if you have the e.g., a protocol like OAEP is used to additionally
RESEARCH Open Access Anonymous gateway-oriented password
The Dangers of Key Reuse Practical Attacks on IPsec IKE
Many protocols like SSH, however any encryption algorithm is vulnerable to this type of attack. (Rivest-Shamir-Adleman)
Mitigating Server Breaches in Password-Based Authentication: Secure and E cient RSA, Mar. 01 2016 executions of the protocol On-line dictionary attack should
A new Bleichenbacher oracle cryptographic attack has been set loose on the world, using a 20-year-old protocol flaw to compromise the Internet Key Exchange (IKE
MiTM on RSA public key encryption. a new pair of public and private RSA keys (pkA , skA ) = ((N, e), d) attack against the key exchange protocol you described
DNS is a protocol that translates a user-friendly and the types of DNS attacks in use today are numerous and quite RSA is a cryptosystem for public-key
I wish to send some small data that RSA alone can encrypt, By using our site, RSA message integrity
A gateway-oriented password-based authenticated key password-based authenticated key exchange a threatening attack against RSA-EPAKE protocol.
Brute force textbook RSA? the Bleichenbacher’s e=3 attack. is in English or something so an attacker could just use a dictionary to check if the decryption
Dictionary based bruteforce on a RSA Private Key. I would like to perform a dictionary attack to try to crack it. Could anyone tell me how to do it?
Doing a dictionary attack on RSA if you could you not simply do a dictionary attack, but is there any advantage to using RSA encryption over hashing if
More than 11 million HTTPS websites imperiled by new decryption attack can use any version of the SSL or TLS protocols, Editor at Ars Technica,
This is a script to perform SSH/SSL RSA private key passphrase enumeration with a dictionary attack. RSA Private Key Passphrase dictionary Protocol (2,701
HTTPS Encryption and Attacks on Authentication in Remote Banking for Internet protocol HTTP using encryption. Asymmetric encryption such as RSA algorithms
Using this exploit, we break these RSA encryption based an offline dictionary attack against the PSK (Pre IKE is one of the most complex protocols in use, and
Encryption padding is necessary to avoid dictionary Vol.4, No. 4 Padding Attacks on RSA attack using LLL algorithm on RSA
More than 11 million HTTPS websites imperiled by new
Brute force textbook RSA? r/crypto – reddit
The keys for the RSA algorithm [/math] by using an agreed-upon reversible protocol The latter property can increase the cost of a dictionary attack
One-third of all HTTPS websites open to DROWN attack Hackers can break TLS using is a “cross-protocol attack that can handshake using 2048- bit RSA in
New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
Attacks on RSA Vlastimil Klíma1 and Tomáš Rosa1,2 1 ICZ, Prague, Czech Republic It is a chosen ciphertext based side channel attack using only the side
Modern servers and clients use the TLS encryption protocol. such an attacker can force the client and server to use RSA key The DROWN attack itself
DROWN: Cross-protocol attack on TLS using SSLv2 (CVE of SSL/TLS sessions between client and server using any version of the protocol and using RSA cipher
RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis GnuPG’s current implementation of RSA. The attack can extract dictionary
Using this exploit, we break these RSA encryption based an offline dictionary attack against the PSK (Pre IKE is one of the most complex protocols in use, and
password-authenticated key exchange protocol is than a trivial online dictionary attack, then one can break RSA Password-authenticated key exchange based on
HTTPS Encryption and Attacks on Authentication in Remote Banking for Internet protocol HTTP using encryption. Asymmetric encryption such as RSA algorithms
Further Results and Considerations on Side Channel Attacks on RSA using the same private RSA key. In the SSL protocol this
Contribute to eazebu/RSAExploits development rsa-wiener-attack Github user pablocelayes has the second is a dictionary that can be used to
col requires more time to execute due to the use of the RSA encryption method An Enhanced Dragonfly Key Exchange Protocol against Offline Dictionary Attack
Adobe Security Operations Manager Kevin Young discusses the benefits his company is seeing from using RSA fastest-growing fraud attack vector. 6/13/2018 – RSA
HTTPS Encryption and Attacks on Authentication in Remote
RSA Blogs
New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
Protocol Interactions and the Chosen Protocol Using the same RSA modulus for both regular and The chosen-protocol attack” is an attack in which some
We see brute force attacks And using a very hard username that makes no sense dictionary Something you know (passwords), something you have (RSA
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
Cryptanalysis of an Efficient RSA-Based Password-Authenticate Key Exchange Protocol against Dictionary Attack
Analysing Password Protocol Security a public key in RSA consisting of a pair (n;e) notion of security of a password protocol against dictionary attacks by
DROWN: Cross-protocol attack on TLS using SSLv2 (CVE of SSL/TLS sessions between client and server using any version of the protocol and using RSA cipher
Many protocols like SSH, however any encryption algorithm is vulnerable to this type of attack. (Rivest-Shamir-Adleman)
Contribute to eazebu/RSAExploits development rsa-wiener-attack Github user pablocelayes has the second is a dictionary that can be used to
Survey on Modular Attack on RSA Algorithm algorithms and protocols in general, Dictionary attack ,it will try also same possibilities but take
password-authenticated key exchange protocol is than a trivial online dictionary attack, then one can break RSA Password-authenticated key exchange based on
HTTPS Encryption and Attacks on Authentication in Remote Banking for Internet protocol HTTP using encryption. Asymmetric encryption such as RSA algorithms
Mitigating Server Breaches in Password-Based Authentication: Secure and E cient RSA, Mar. 01 2016 executions of the protocol On-line dictionary attack should
Modern servers and clients use the TLS encryption protocol. such an attacker can force the client and server to use RSA key The DROWN attack itself
RSA (cryptosystem) Wikipedia
Protocol Interactions and the Chosen Protocol Attack
RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis GnuPG’s current implementation of RSA. The attack can extract dictionary
ROBOT Attack: RSA TLS crypto attack worked against Facebook, PayPal, and tens of 100 top domains
Are very short messages secure using Public Key Doing a dictionary attack on RSA if you have the e.g., a protocol like OAEP is used to additionally
I wish to send some small data that RSA alone can encrypt, By using our site, RSA message integrity
The keys for the RSA algorithm are smaller than by using an agreed-upon reversible protocol known as the cost of a dictionary attack beyond the
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
RSA (cryptosystem) Wikipedia
Juniper Networks Cross-protocol attack on TLS using
… (Rivest–Shamir–Adleman) < n by using an agreed-upon reversible protocol known chosen ciphertext attack, against RSA-encrypted messages using the
Tibor Jager and colleagues discovered that it is possible to use a cross-protocol Bleichenbacher attack against TLS 1 ROBOT Attack: RSA TLS crypto attack
DNS is a protocol that translates a user-friendly and the types of DNS attacks in use today are numerous and quite RSA is a cryptosystem for public-key
A new Bleichenbacher oracle cryptographic attack has been set loose on the world, using a 20-year-old protocol flaw to compromise the Internet Key Exchange (IKE
DROWN: Cross-protocol attack on TLS using SSLv2 (CVE of SSL/TLS sessions between client and server using any version of the protocol and using RSA cipher
1 Partial Key Exposure Attack On Low-Exponent RSA Eric W. Everstine 1 Introduction Let N = pq be an RSA modulus with e, d encryption exponents such that
Using this exploit, we break these RSA encryption based an offline dictionary attack against the PSK (Pre IKE is one of the most complex protocols in use, and
Doing a dictionary attack on RSA if you could you not simply do a dictionary attack, but is there any advantage to using RSA encryption over hashing if
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
He first turns M into an integer 0 < m < n by using an agreed-upon reversible protocol attack, against RSA-encrypted messages using a dictionary attack
A gateway-oriented password-based authenticated key password-based authenticated key exchange a threatening attack against RSA-EPAKE protocol.
Are very short messages secure using Public Key Doing a dictionary attack on RSA if you have the e.g., a protocol like OAEP is used to additionally
Dictionary based bruteforce on a RSA Private Key. I would like to perform a dictionary attack to try to crack it. Could anyone tell me how to do it?
More than 11 million HTTPS websites imperiled by new
RSA (cryptosystem) Wikipedia
Cross-protocol attack on TLS using SSLv2 (DROWN) (CVE-2016 EXPORT cipher suites as a Bleichenbacher RSA Cross-protocol attack on TLS using SSLv2
Breaking RSA OAEP with Manger’s attack
Attacks on RSA Vlastimil Klíma1 and Tomáš Rosa1,2 1 ICZ, Prague, Czech Republic It is a chosen ciphertext based side channel attack using only the side
RSA (cryptosystem) Wikipedia
RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis
Padding attacks on RSA ScienceDirect
Contribute to eazebu/RSAExploits development rsa-wiener-attack Github user pablocelayes has the second is a dictionary that can be used to
Researchers Break IPsec VPN Connections with 20-Year-Old
Protocols and Privacy Amplification quadibloc.com
Encryption padding is necessary to avoid dictionary Vol.4, No. 4 Padding Attacks on RSA attack using LLL algorithm on RSA
An Enhanced Dragonfly Key Exchange Protocol against
security Dictionary based bruteforce on a RSA Private
Dictionary based bruteforce on a RSA Private Key. I would like to perform a dictionary attack to try to crack it. Could anyone tell me how to do it?
RSA (cryptosystem) Wikipedia
RSA (algorithm) Facts for Kids Kiddle encyclopedia
12.1 Public-Key Cryptography 3 12.2 The Rivest-Shamir-Adleman 12.9 The Security of RSA — The Mathematical Attack 55 on the protocol.
Cisco patches router OS against new crypto attack on
RSA algorithm Simple English Wikipedia the free
Dictionary based bruteforce on a RSA Private Key. I would like to perform a dictionary attack to try to crack it. Could anyone tell me how to do it?
security Dictionary based bruteforce on a RSA Private
DROWN: Cross-protocol attack on TLS using SSLv2 (CVE of SSL/TLS sessions between client and server using any version of the protocol and using RSA cipher
DROWN Cross-protocol attack on TLS using SSLv2 (CVE-2016
RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis GnuPG’s current implementation of RSA. The attack can extract dictionary
rsa Is this chat protocol safe? – Cryptography Stack
Practical Bleichenbacher Attacks on IPsec IKE
Anonymous gateway-oriented password-based authenticated
DNS is a protocol that translates a user-friendly and the types of DNS attacks in use today are numerous and quite RSA is a cryptosystem for public-key
Brute force textbook RSA? r/crypto – reddit
Partial Key Exposure Attack On Low-Exponent RSA
M5410 Protocol Failures UC Denver
New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
ROBOT Attack RSA TLS crypto attack worked against
We see brute force attacks And using a very hard username that makes no sense dictionary Something you know (passwords), something you have (RSA
Protocols and Privacy Amplification quadibloc.com
fficient and Leakage-Resilient RSA-Based Authenticated Key
What is DNS attack? Definition from WhatIs.com
New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
Juniper Networks Cross-protocol attack on TLS using
Weakness in a RSA-based password authenticated key
Protocol Interactions and the Chosen Protocol Attack
Encryption padding is necessary to avoid dictionary Vol.4, No. 4 Padding Attacks on RSA attack using LLL algorithm on RSA
DROWN Breaking TLS using SSLv2 DROWN Attack Paper
HTTPS Encryption and Attacks on Authentication in Remote
The Dangers of Key Reuse Practical Attacks on IPsec IKE
Doing a dictionary attack on RSA if you could you not simply do a dictionary attack, but is there any advantage to using RSA encryption over hashing if
rsa German translation – Linguee
Contribute to eazebu/RSAExploits development rsa-wiener-attack Github user pablocelayes has the second is a dictionary that can be used to
RSA (algorithm) Facts for Kids Kiddle encyclopedia
New Approaches to Password Authenticated Key Exchange based line dictionary attack against RSA-based RSA public exponent e. In the protocol
Attack Methods to Steal Digital Secrets Microchip Technology
fficient and Leakage-Resilient RSA-Based Authenticated Key
The Dangers of Key Reuse Practical Attacks on IPsec IKE
This is a script to perform SSH/SSL RSA private key passphrase enumeration with a dictionary attack. RSA Private Key Passphrase dictionary Protocol (2,701
rsa German translation – Linguee
RSA Blogs
col requires more time to execute due to the use of the RSA encryption method An Enhanced Dragonfly Key Exchange Protocol against Offline Dictionary Attack
DROWN Breaking TLS using SSLv2 DROWN Attack Paper
Cryptography Quick Guide Tutorials Point
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
RESEARCH Open Access Anonymous gateway-oriented password
RSA is a cryptosystem for public-key encryption, and is widely used for securing sensitive data, particularly when being sent over an insecure network such as the
Brute force textbook RSA? r/crypto – reddit
Attack Methods to Steal Digital Secrets Microchip Technology
Are very short messages secure using Public Key Doing a dictionary attack on RSA if you have the e.g., a protocol like OAEP is used to additionally
GitHub eazebu/RSAExploits
The keys for the RSA algorithm are smaller than by using an agreed-upon reversible protocol known as the cost of a dictionary attack beyond the
security Dictionary based bruteforce on a RSA Private
Anonymous gateway-oriented password-based authenticated key A gateway-oriented password-based authenticated attack against RSA-EPAKE protocol.
Attack Methods to Steal Digital Secrets Microchip Technology
Breaking RSA OAEP with Manger’s attack
RSA Blogs
Adobe Security Operations Manager Kevin Young discusses the benefits his company is seeing from using RSA fastest-growing fraud attack vector. 6/13/2018 – RSA
DROWN Cross-protocol attack on TLS using SSLv2 (CVE-2016
The keys for the RSA algorithm [/math] by using an agreed-upon reversible protocol The latter property can increase the cost of a dictionary attack
Further Results and Considerations on Side Channel Attacks
MiTM on RSA public key encryption. a new pair of public and private RSA keys (pkA , skA ) = ((N, e), d) attack against the key exchange protocol you described
RSA Wikis (The Full Wiki)
The ROBOT Attack Return of Bleichenbacher’s Oracle Threat
protocol design RSA message integrity – Cryptography
Mitigating Server Breaches in Password-Based Authentication: Secure and E cient RSA, Mar. 01 2016 executions of the protocol On-line dictionary attack should
CrypTool Presentation Public Key Cryptography scribd.com
ROBOT Attack: RSA TLS crypto attack worked against Facebook, PayPal, and tens of 100 top domains
CertSimple So you’re making an RSA key for an HTTPS
The ROBOT Attack Return of Bleichenbacher’s Oracle Threat
Adobe Security Operations Manager Kevin Young discusses the benefits his company is seeing from using RSA fastest-growing fraud attack vector. 6/13/2018 – RSA
An Enhanced Dragonfly Key Exchange Protocol against
Researchers Break IPsec VPN Connections with 20-Year-Old
Adobe Security Operations Manager Kevin Young discusses the benefits his company is seeing from using RSA fastest-growing fraud attack vector. 6/13/2018 – RSA
Analysing Password Protocol Security Against Off-line
DROWN Breaking TLS using SSLv2 DROWN Attack Paper
Further Results and Considerations on Side Channel Attacks on RSA using the same private RSA key. In the SSL protocol this
Survey on Modular Attack on RSA Algorithm IJCEM
Vulnerable IPSec IKE implementations in Cisco, Huawei, ZyXel and Clavister networking devices can allow attackers to decrypt connections.
“DROWN Cross-protocol attack on TLS using SSLv2 – CVE
RSA Blogs
Cracking short RSA keys. /** * Computes the factors of n given d and e. * Given are the public RSA key A Variant of Wiener’s Attack on RSA;
An Enhanced Dragonfly Key Exchange Protocol against
Survey on Modular Attack on RSA Algorithm algorithms and protocols in general, Dictionary attack ,it will try also same possibilities but take
DROWN protocol flaw allows hackers to break TLS using
Anonymous gateway-oriented password-based authenticated
1 Partial Key Exposure Attack On Low-Exponent RSA Eric W. Everstine 1 Introduction Let N = pq be an RSA modulus with e, d encryption exponents such that
RSA Wikis (The Full Wiki)
RSA provides Business-Driven Security solutions for advanced threat detection and cyber incident response, identity and access management, and GRC.
DROWN Attack
Lecture 12 Public-Key Cryptography and the RSA Algorithm
Cryptography Quick Guide Tutorials Point
… the encrypted first session key would be of no use for a dictionary attack. protocol is to use the common them using B’s RSA key as many
protocol design RSA message integrity – Cryptography
Practical Bleichenbacher Attacks on IPsec IKE
DNS is a protocol that translates a user-friendly and the types of DNS attacks in use today are numerous and quite RSA is a cryptosystem for public-key
Possible Attacks on RSA Tripod.com
password-authenticated key exchange protocol is than a trivial online dictionary attack, then one can break RSA Password-authenticated key exchange based on
math Cracking short RSA keys – Stack Overflow
Encryption padding is necessary to avoid dictionary Vol.4, No. 4 Padding Attacks on RSA attack using LLL algorithm on RSA
Tw en t y Y ears of A ttac ks on the RSA Cryptosystem
Survey on Modular Attack on RSA Algorithm IJCEM
encryption Doing a dictionary attack on RSA if you have
Tibor Jager and colleagues discovered that it is possible to use a cross-protocol Bleichenbacher attack against TLS 1 ROBOT Attack: RSA TLS crypto attack
HTTPS Encryption and Attacks on Authentication in Remote
CrypTool Presentation. (on hybrid encryption protocol) Attack on RSA using lattice reduction Random analysis with 3 Dictionary attack with variants (e.
Analysing Password Protocol Security Against Off-line
An Enhanced Dragonfly Key Exchange Protocol against
rsa Is this chat protocol safe? – Cryptography Stack