Spins security protocols for sensor networks pdf
Abstract. Sensor network is a dominant technology among different wireless communication technologies due to its great deal of efficiency. Security is the critical issue for every types of network whether it is sensor networks or other networks. So far, many of the researchers have thought to
Abstract: In wireless sensor networks (WSNs), Security is critical for many sensor network applications, such as military target tracking and security monitoring. In particular, providing authentication to small sensor nodes is challenging, due to the limited capabilities of sensor …
sensor networks are low power, low-memory, low-energy and having bulky scaled nodes. Due to this Due to this various facts the existing security algorithms are not appropriate for current applications.
based communication protocols for homogeneous wireless sensor networks consisting of sensor nodes with severely limited resources, and propose a security solution for LEACH, a protocol where clusters are formed dynamically and periodically.
Abstract. Wireless sensor networks will be widely deployed in the near future. While much research has focused on making these networks feasible and useful, security has received little attention. We present a suite of security protocols optimized for sensor networks: SPINS. SPINS has two secure
security requirements for sensor networks for this paper. Section 3 provides a look at key Section 3 provides a look at key distribution techniques for groups of varying size.
Wireless Networks 8, 521–534, 2002 2002 Kluwer Academic Publishers. Manufactured in The Netherlands. SPINS: Security Protocols for Sensor Networks ADRIAN PERRIG, ROBERT…
A Review of various security protocols in Wireless Sensor Network Anupma Sangwan1, Deepti Sindhu2, An ideal sensor network protocol should provide data authentication, confidentiality, integrity of data and protection from replay. The security and efficiency being the basic parameters used to design a new sensor network protocol. A wireless sensor node integrates one or more sensors, …
22/08/2011 · Student Seminar Report & Project Report With Presentation (PPT,PDF,DOC,ZIP) thread spins spins security protocols for sensor networks
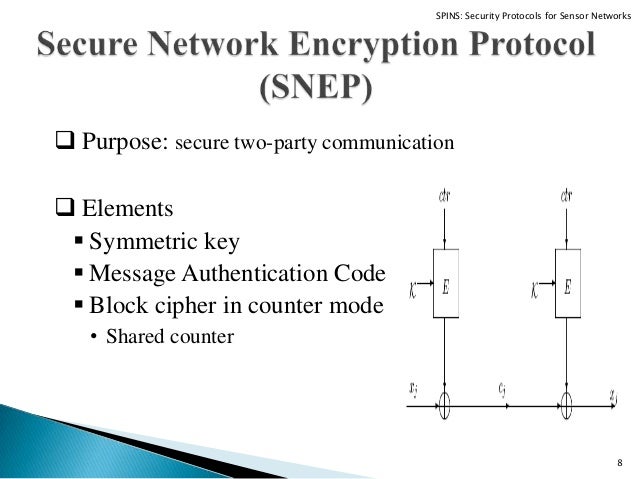
Algebraic specification languages are formal methods that provide a rigorous basis for modeling of several systems. Security protocols are safety critical systems that need to be verified before their implementation. In this paper we have formally specified sensor network encryption protocol (SNEP
As sensor networks edge closer towards wide-spread deployment, security issues become a central concern. So far, much research has focused on making sensor networks feasible and useful, and has not concentrated on security.
Security has become a challenge in wireless sensor networks. Low capabilities of devices, in terms of computational power and energy consumption, make difficult using traditional security protocols.
SPINS: Security Protocols for Sensor Networks Adrian Perrig et al. University of California, Berkeley Mobicom 2001 Presenter: Ryan Babbitt Outline Background Protocols SNEP μTESLA Example applications Authenticated Routing Node-to-node key agreement Conclusions Background Sensor networks Nodes Base stations Communication channel Communication
Security Protocol for Wireless Sensor Networks • 635 [Hespanha et al. 1999; Vidal et al. 2002], in which a group of pursuers attempts to track and capture moving evaders.Asensor network …
sensor nodes in terms of energy, storage and computational ability, many security issues have arisen in such applications. As a result, many solutions and approaches have been proposed for …
Spin protocols ppt Wireless Sensor Network Computer

Light Weight Security Protocol for Wireless Sensor Network
In thefuture, we envision wireless sensor networks being used for emer-gency and life-critical systems – and here the questions of securityare foremost.This paper presents a set of Security Protocols for Sensor Net-works, SPINS.
Wireless sensor networks will be widely deployed in the near future. While much research has focused on making these networks feasible and useful, security has received little attention.
Abstract. As sensor networks edge closer towards wide-spread deployment, security issues become a central concern. So far, much research has focused on making sensor networks feasible and useful, and has not concentrated on security.
In recent years, wireless sensor network (WSN) is employed in many application areas such as monitoring, tracking, and controlling. For many applications of WSN, security …
base the security architecture on symmetric key cryptography reduce memory usage by re-using code – all crypto primitives are built out of from a single block cipher
Security in sensor networks is possible in a limited way, but it requires resources and generates overhead, which shortens the overall lifetime of the network. References Adrian Perrig, Robert Szewczyk, J.D. Tygar, Victor Wen, David E. Culler: SPINS – Security Protocols for Sensor Networks
Paper summary; SPINS: Security Protocols for Sensor Networks Slideshare uses cookies to improve functionality and performance, and to provide you with relevant advertising. If you continue browsing the site, you agree to the use of cookies on this website.
Routing Protocols in Wireless Sensor Networks – A Survey Shio Kumar Singh 1, M P Singh 2, Wireless Sensor Networks, Routing Protocols, Cluster Head 1. Introduction Wireless sensor network (WSN) is widely considered as one of the most important technologies for the twenty-first century [1]. In the past decades, it has received tremendous attention from both academia and industry all over
0 Votos desfavoráveis, marcar como não útil. SPINS: Security Protocols for Sensor Networks. Enviado por c4sudhir
SPINS has two secure building blocks: SNEP and #TESLA. SNEP provides the following important baseline security primitives: Data confidentiality, two-party data authentication, and data freshness. A particularly hard problem is to provide efficient broadcast authentication, which is an important mechanism for sensor networks. #TESLA is a new protocol which provides authenticated …
security scheme in wireless sensor networks is created by the This work was supported by MIC and ITRC Project size of sensors, consequently the processing power, memory
SPINS: SECURITY PROTOCOLS FOR SENSOR NETWORKS 523 We do have an advantage with sensor networks, because most communication involves the base station and is not be-
SPINS: Security Protocols for Sensor Networks An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other …
sensor node, limit both the security and the performance of a sensor network. Confidentiality, data integrity, and authentication services must be supported to prevent adversaries from compromising the sensor network, but advanced
The paper studies an authenticated routing pro- protocols in the sensor networks. tocol and a two-party key agreement protocol, and demonstrates that our security building blocks greatly facilitate the implementa- Communication architecture tion of a complete security solution for a sensor network. A common characteristic of sensor networks is their severely Generally, the sensor nodes

Sensor network is a dominant technology among different wireless communication technologies due to its great deal of efficiency. Security is the critical issue for every types of network whether
An Evaluation of Security Protocols on Wireless Sensor Network Abu Shohel Ahmed Helsinki University of Technology aahmed@cc.hut.fi Abstract In recent years, Wireless Sensor Network (WSN) is …
1 Security Protocols for Sensor Networks Presented by Vijay Bhuse CS603, Spring 2004 Material liberally borrowed from web • Adrian Perrig, Robert Szewczyk, Victor Wen, David Culler, J. D.
Forum Session: Security for Wireless Sensor Networks David Carman Network Associates Laboratories David_Carman@nai.com Daniel Coffin BBN Technologies
4 7 Research problem cont’d nSensor networks to be used for emergency and life critical systems as well as military applications nHence, security is first and foremost.
SPIN (Sensor Protocols for Information via negotiation), is a family of negotiation-based information dissemination protocols suitable for wireless sensor networks. This is a straightforward protocol …
Automatic Security Protocol Generation and Verification. A First Step towards the Automatic Generation of Security Protocols PS, PS.GZ, PDF, HTML, BIB, with Dawn Song.
SPIN: A Data Centric Protocol For Wireless Sensor Networks 1Amitoj Kaur, 2Gursimrat Singh, 3Jagroop Kaur 1,2Student of M.Tech Computer Science, Punjabi University Patiala
SPINS Security protocols for sensor networks UC
Security in the sensor network is a significant challenge as the resources in sensor devices are not sufficient for operating traditional security protocols. This weakness
Introduction Full paper: Postscript, PS.GZ, PDF. SPINS: Security Protocols for Sensor Networks. Adrian Perrig, Robert Szewczyk, Victor Wen, David Culler, J. D. Tygar
SPINS: Security Protocols for Sensor Networks R.Geetha Cse-A,3rdyear IFET college of engineering Villupuram geethaifet@gmail.com Abstract. Wireless sensor networks will be widely deployed
Security in Wireless Sensor Networks – A Study L. Ertaul1, M. Ganta2 problems in WSNs and discusses the security protocols based on three different security mechanisms: Security Protocols for WSNs (SPINS), which uses symmetric key cryptography, then TinySec, which is based on Link layer encryption, and later TinyPK (the Public Key Infrastructure solution). This study also presents the
On the Development of Adaptive and Self-dependent Secure Routing Protocol (ASSP) for Wireless Sensor Networks Jamal N. Al-Karaki 1, Samer Khasawneh 1, Mohammad Alrousan 2
“SPINS: Security Protocols for Sensor Networks,” MobiCom 2001, pp.189-199, July 2001. 2 Outline Introduction SPINS Security Building Blocks Application Evaluation Conclusion. 3 Introduction (1/2) This paper presents a suite of security building blocks optimized for resource constrained environments and wireless communication. This approach is considered to be a master key theorem which
spins by magna, sensor network conferences, network security p, whats the tricks to a fat man spooky spins machine, thread spins spins security protocols for sensor networks, the spins, sensor network protocol, – protocol p series helicopter manual FORMAL ANALYSIS OF SECURITY PROTOCOLS FOR WIRELESS SENSOR NETWORKS node in the sequence. A length of a path is the number of edges in the path.
SPINS: Security Protocols for Sensor Networks Adrian Perrig, Robert Szewczyk, Victor Wen, David Culler, J. D. Tygar Department of Electrical Engineering and Computer Sciences
“SPINS: Security protocols for sensor networks.” [ACM Journal of] Wireless Networks, 8:5, September 2002, pp. 521-534 Abstract Wireless sensor networks will be widely deployed in …
Neeli Rashmi Prasad, Associate Professor and Head of Wireless Security and Sensor Networks Lab., part of Wireless Network including Embedded systems Group (WING), Center for TeleInfrastruktur (CTIF), Aalborg University, Aalborg, Denmark.
SPINS: SECURITY PROTOCOLS FOR SENSOR NETWORKS 523 We do have an advantage with sensor networks, because 3. Requirements for sensor network security most communication involves the base station and is not be- tween two local nodes. The communication patterns within This section formalizes the security properties required by our network fall into three categories: sensor networks…
SPINS: Security Protocols for Sensor Networks 1. Department of Computer Engineering NAVSAHYADRI EDUCATION SOCIETY’S GROUP OF INSTITUTES, FACULTY OF ENGINEERING Naigaon-412206, Tal.
Read “SPINS: security protocols for sensor networks” on DeepDyve, the largest online rental service for scholarly research with thousands of academic publications available at your fingertips.
Important..!About full seminar pdf in spins security protocols for sensor networks is Not Asked Yet ? .. Please ASK FOR full seminar pdf in spins security protocols for sensor networks BY CLICK HERE….Our Team/forum members are ready to help you in free of cost…
The security of sensor networks is a challenging area. Key management is one of the crucial parts in constructing the security among sensor nodes. However, key management protocols require a great deal of energy consumption, particularly in the transmission of initial key negotiation messages. In this paper, we examine three previously published sensor network security schemes: SPINS and C&R
We are developing an Open Experimental software/hardware Platform for Network Embedded Systems Technology research that will accelerate the development of algorithms, services, and their composition into challenging applications dramatically.
This article presents a set of Security Protocols for Sensor Networks, SPINS. The chief contributions of this article are: Exploring the challenges for security in sensor networks. Designing and developing TESLA (the “micro” version of TESLA), providing authenticated streaming broadcast. Designing and developing SNEP (Secure Network Encryption Protocol) providing data con dentiality, two
Wireless sensor networks will be widely deployed in the near future. While much research has focused on making these networks feasible and useful, security has received little attention. We present a suite of security protocols optimized for sensor networks: SPINS. SPINS has two secure building
1 SPINS: Security Protocols for Sensor Networks Adrian Perrig, Robert Szewczyk, J.D. Tygar, Victor Wen, and David Culler Department of Electrical Engineering &
Security Framework for Wireless Sensor Networks Springer
Security Protocols for Wireless Sensor Network – Download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. Scribd is the world’s largest social reading and publishing site.
For example, SPINS [2] used RC5 [3] as the block cipher. TinySec [4] used Skipjack [5] as the default block cipher. Neighborhood Based Security Protocol is used to provide authentication in Wireless Sensor Network’s(WSN).NEKAP [6], a design of link layer key agreement protocol for sensor networks. NEKAP can provide the Confidentiality but sometimes this protocol fails to provide
Seminar Topic: SPIN – Protocols for Wireless Sensor Networks Motivation • Dissemination is the process of distributing individual sensor observations to the whole network, treating all sensors as sink nodes • Limited supply of energy • Limited computational power • Limited communication resources
SPINS Security protocols for sensor networks Dhanraj

Security Protocols for Wireless Sensor Network Network
LiSP A Lightweight Security Protocol for Wireless Sensor
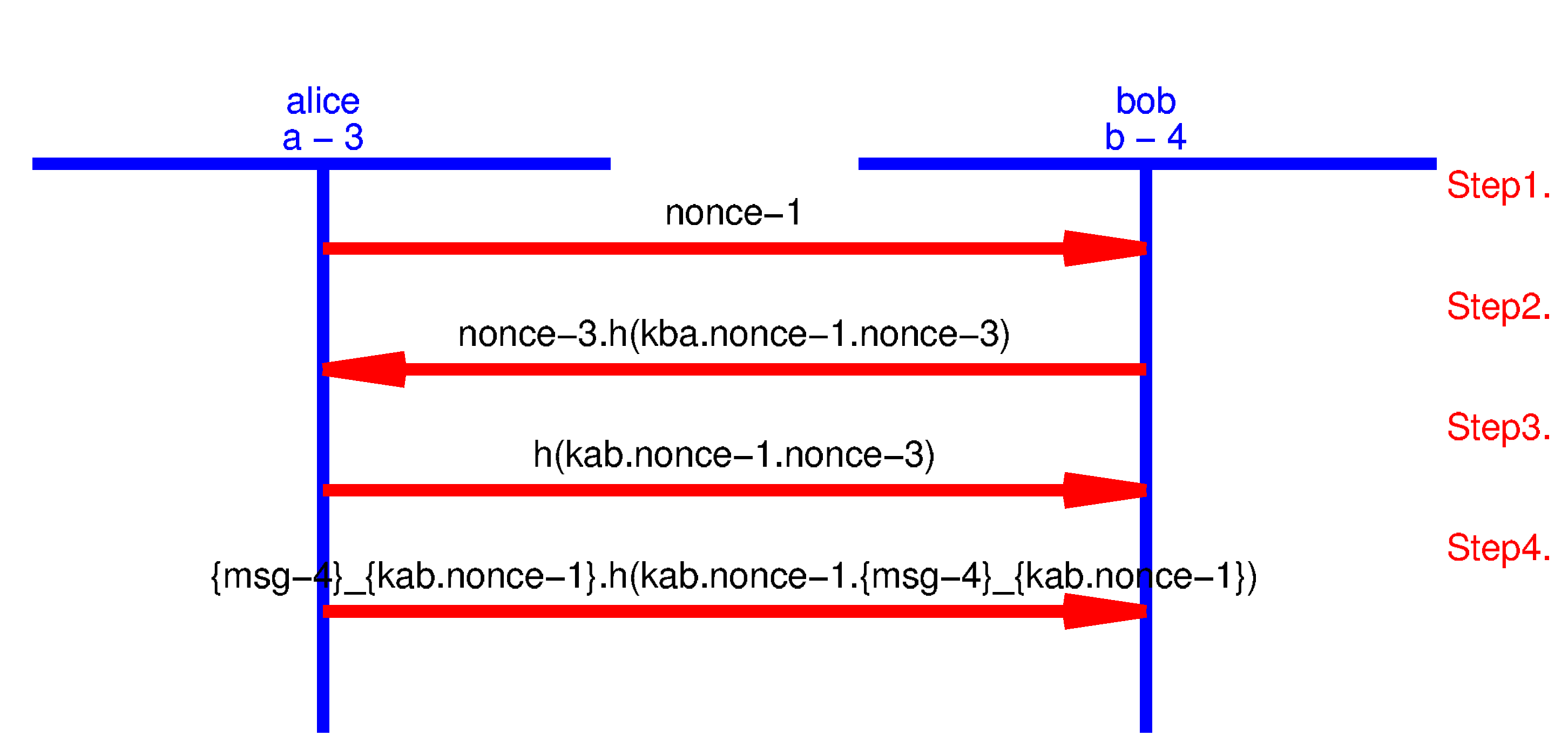
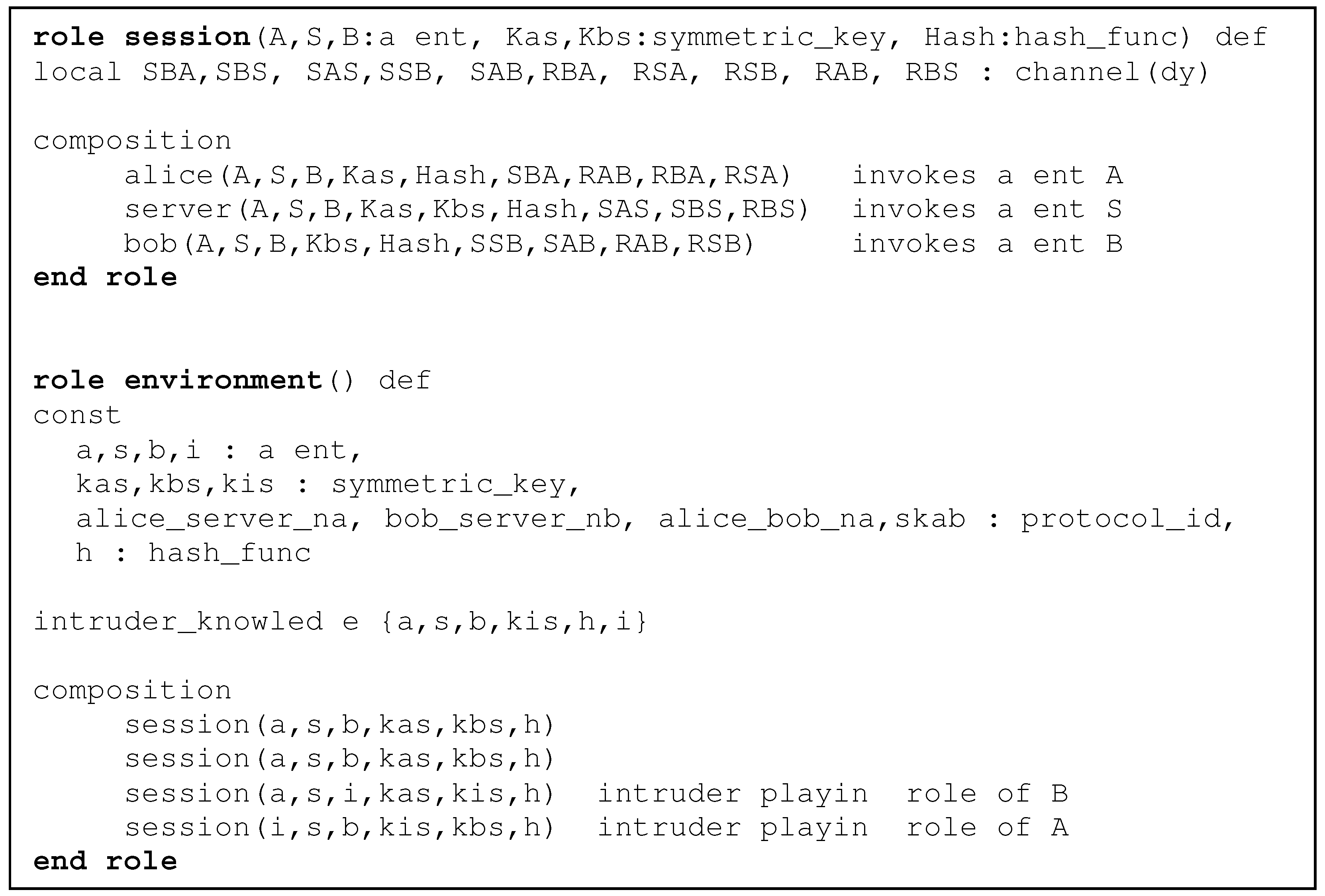
Verifying Security Protocols for Sensor Networks Using
Security in Sensor Networks Computer Science

SPINS security protocols for sensor networks 10.1145
SPINS Security Protocols for Sensor Networks BME-HIT
– ASSP Adaptive Self-dependent Security Protocol for
FORMAL ANALYSIS OF SECURITY PROTOCOLS FOR WIRELESS SENSOR

SPIN A Data Centric Protocol For Wireless Sensor Networks
Energy efficient security protocols for wireless sensor
4 7 Research problem cont’d nSensor networks to be used for emergency and life critical systems as well as military applications nHence, security is first and foremost.
full seminar pdf in spins security protocols for sensor
(PDF) SPINS Security Protocols for Sensor Networks
security requirements for sensor networks for this paper. Section 3 provides a look at key Section 3 provides a look at key distribution techniques for groups of varying size.
spins security protocols for sensor networks docx
thread spins spins security protocols for sensor networks
We are developing an Open Experimental software/hardware Platform for Network Embedded Systems Technology research that will accelerate the development of algorithms, services, and their composition into challenging applications dramatically.
REVIEW ON SECURITY PROTOCOLS IN WIRELESS SENSOR NETWORKS
Verifying Security Protocols for Sensor Networks Using
Spin protocols ppt Wireless Sensor Network Computer
SPIN (Sensor Protocols for Information via negotiation), is a family of negotiation-based information dissemination protocols suitable for wireless sensor networks. This is a straightforward protocol …
A Review of various security protocols in Wireless Sensor
0 Votos desfavoráveis, marcar como não útil. SPINS: Security Protocols for Sensor Networks. Enviado por c4sudhir
SPINS Security Protocols for Sensor Networks BME-HIT
SPINS Security protocols for sensor networks Dhanraj
An Evaluation of Security Protocols on Wireless Sensor Network Abu Shohel Ahmed Helsinki University of Technology aahmed@cc.hut.fi Abstract In recent years, Wireless Sensor Network (WSN) is …
SPINS Security Protocols for Sensor Networks docx
LiSP A Lightweight Security Protocol for Wireless Sensor
On the Development of Adaptive and Self-dependent Secure Routing Protocol (ASSP) for Wireless Sensor Networks Jamal N. Al-Karaki 1, Samer Khasawneh 1, Mohammad Alrousan 2
SECURITY IN WIRELESS SENSOR NETWORKS A FORMAL
SPINS has two secure building blocks: SNEP and #TESLA. SNEP provides the following important baseline security primitives: Data confidentiality, two-party data authentication, and data freshness. A particularly hard problem is to provide efficient broadcast authentication, which is an important mechanism for sensor networks. #TESLA is a new protocol which provides authenticated …
LiSP A Lightweight Security Protocol for Wireless Sensor
SECURITY IN WIRELESS SENSOR NETWORKS A FORMAL
Security Protocols for Wireless Sensor Network Network
Abstract: In wireless sensor networks (WSNs), Security is critical for many sensor network applications, such as military target tracking and security monitoring. In particular, providing authentication to small sensor nodes is challenging, due to the limited capabilities of sensor …
Spin protocols ppt Wireless Sensor Network Computer
thread spins spins security protocols for sensor networks
SPINS Security Protocols for Sensor Networks [PDF Document]
Abstract. Wireless sensor networks will be widely deployed in the near future. While much research has focused on making these networks feasible and useful, security has received little attention. We present a suite of security protocols optimized for sensor networks: SPINS. SPINS has two secure
SPINS Security protocols for sensor networks Dhanraj
An Improved- SPIN Protocol for Wireless Sensor Networks
CiteSeerX — SPINS Security Protocols for Sensor Networks
SPINS: SECURITY PROTOCOLS FOR SENSOR NETWORKS 523 We do have an advantage with sensor networks, because 3. Requirements for sensor network security most communication involves the base station and is not be- tween two local nodes. The communication patterns within This section formalizes the security properties required by our network fall into three categories: sensor networks…
thread spins spins security protocols for sensor networks
SPINS Security Protocols for Sensor Networks [PDF Document]
based communication protocols for homogeneous wireless sensor networks consisting of sensor nodes with severely limited resources, and propose a security solution for LEACH, a protocol where clusters are formed dynamically and periodically.
Forum Session Security for Wireless Sensor Networks
SPINS Security Protocols for Sensor Networks People
Algebraic specification languages are formal methods that provide a rigorous basis for modeling of several systems. Security protocols are safety critical systems that need to be verified before their implementation. In this paper we have formally specified sensor network encryption protocol (SNEP
SPINS security protocols for sensor networks 10.1145
security scheme in wireless sensor networks is created by the This work was supported by MIC and ITRC Project size of sensors, consequently the processing power, memory
KEY DISTRIBUTION AND DISTRIBUTED INTRUSION DETECTION
SPINS Security protocols for sensor networks Dhanraj
SECURITY IN WIRELESS SENSOR NETWORKS A FORMAL
Security Protocols for Wireless Sensor Network – Download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. Scribd is the world’s largest social reading and publishing site.
REVIEW ON SECURITY PROTOCOLS IN WIRELESS SENSOR NETWORKS
Security Protocols for Sensor Networks wmich.edu
Energy efficient security protocols for wireless sensor
SPINS: SECURITY PROTOCOLS FOR SENSOR NETWORKS 523 We do have an advantage with sensor networks, because 3. Requirements for sensor network security most communication involves the base station and is not be- tween two local nodes. The communication patterns within This section formalizes the security properties required by our network fall into three categories: sensor networks…
Forum Session Security for Wireless Sensor Networks
Security Protocols for Wireless Sensor Network – Download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. Scribd is the world’s largest social reading and publishing site.
Forum Session Security for Wireless Sensor Networks
spins security protocols for sensor networks docx
SPINS Security Protocols for Sensor Networks CORE
base the security architecture on symmetric key cryptography reduce memory usage by re-using code – all crypto primitives are built out of from a single block cipher
thread spins spins security protocols for sensor networks
KEY DISTRIBUTION AND DISTRIBUTED INTRUSION DETECTION
In thefuture, we envision wireless sensor networks being used for emer-gency and life-critical systems – and here the questions of securityare foremost.This paper presents a set of Security Protocols for Sensor Net-works, SPINS.
Network Security Group ETH Zurich
Algebraic specification languages are formal methods that provide a rigorous basis for modeling of several systems. Security protocols are safety critical systems that need to be verified before their implementation. In this paper we have formally specified sensor network encryption protocol (SNEP
Security protocols in sensor networks hu-berlin.de
Abstract. As sensor networks edge closer towards wide-spread deployment, security issues become a central concern. So far, much research has focused on making sensor networks feasible and useful, and has not concentrated on security.
Security in Sensor Networks Computer Science
0 Votos desfavoráveis, marcar como não útil. SPINS: Security Protocols for Sensor Networks. Enviado por c4sudhir
full seminar pdf in spins security protocols for sensor
Secure Language-Based Adaptive Platform for WEBS
Read “SPINS: security protocols for sensor networks” on DeepDyve, the largest online rental service for scholarly research with thousands of academic publications available at your fingertips.
SPINS Security Protocols for Sensor Networks CORE
Wireless Networks 8, 521–534, 2002 2002 Kluwer Academic Publishers. Manufactured in The Netherlands. SPINS: Security Protocols for Sensor Networks ADRIAN PERRIG, ROBERT…
LiSP A Lightweight Security Protocol for Wireless Sensor
SPINS Security Protocols for Sensor Networks CORE
Network Security Group ETH Zurich
The paper studies an authenticated routing pro- protocols in the sensor networks. tocol and a two-party key agreement protocol, and demonstrates that our security building blocks greatly facilitate the implementa- Communication architecture tion of a complete security solution for a sensor network. A common characteristic of sensor networks is their severely Generally, the sensor nodes
Energy efficient security protocols for wireless sensor
Forum Session Security for Wireless Sensor Networks
SPINS Security protocols for sensor networks Dhanraj
SPINS has two secure building blocks: SNEP and #TESLA. SNEP provides the following important baseline security primitives: Data confidentiality, two-party data authentication, and data freshness. A particularly hard problem is to provide efficient broadcast authentication, which is an important mechanism for sensor networks. #TESLA is a new protocol which provides authenticated …
SPINS security protocols for sensor networks 10.1145
SPINS Security Protocols for Sensor Networks [PDF Document]
Security in sensor networks is possible in a limited way, but it requires resources and generates overhead, which shortens the overall lifetime of the network. References Adrian Perrig, Robert Szewczyk, J.D. Tygar, Victor Wen, David E. Culler: SPINS – Security Protocols for Sensor Networks
FORMAL ANALYSIS OF SECURITY PROTOCOLS FOR WIRELESS SENSOR
security scheme in wireless sensor networks is created by the This work was supported by MIC and ITRC Project size of sensors, consequently the processing power, memory
spins security protocols for sensor networks docx
SPINS Security Protocols for Sensor Networks [PDF Document]
Security Framework for Wireless Sensor Networks Springer
This article presents a set of Security Protocols for Sensor Networks, SPINS. The chief contributions of this article are: Exploring the challenges for security in sensor networks. Designing and developing TESLA (the “micro” version of TESLA), providing authenticated streaming broadcast. Designing and developing SNEP (Secure Network Encryption Protocol) providing data con dentiality, two
Security Protocols for Wireless Sensor Network Network
FORMAL ANALYSIS OF SECURITY PROTOCOLS FOR WIRELESS SENSOR
REVIEW ON SECURITY PROTOCOLS IN WIRELESS SENSOR NETWORKS
Security in Wireless Sensor Networks – A Study L. Ertaul1, M. Ganta2 problems in WSNs and discusses the security protocols based on three different security mechanisms: Security Protocols for WSNs (SPINS), which uses symmetric key cryptography, then TinySec, which is based on Link layer encryption, and later TinyPK (the Public Key Infrastructure solution). This study also presents the
Spin protocols ppt Wireless Sensor Network Computer
SPINS Security Protocols For Sensor Networks
Security in Wireless Sensor Networks – A Study
based communication protocols for homogeneous wireless sensor networks consisting of sensor nodes with severely limited resources, and propose a security solution for LEACH, a protocol where clusters are formed dynamically and periodically.
Security Protocols for Wireless Sensor Network Network
Security Protocol for Wireless Sensor Networks • 635 [Hespanha et al. 1999; Vidal et al. 2002], in which a group of pursuers attempts to track and capture moving evaders.Asensor network …
SPINS Security Protocols for Sensor Networks SlideShare
Wireless sensor networks will be widely deployed in the near future. While much research has focused on making these networks feasible and useful, security has received little attention. We present a suite of security protocols optimized for sensor networks: SPINS. SPINS has two secure building
Security protocols in sensor networks hu-berlin.de
SPINS: SECURITY PROTOCOLS FOR SENSOR NETWORKS 523 We do have an advantage with sensor networks, because most communication involves the base station and is not be-
SPINS Security Protocols for Sensor Networks [PDF Document]
A Review of various security protocols in Wireless Sensor Network Anupma Sangwan1, Deepti Sindhu2, An ideal sensor network protocol should provide data authentication, confidentiality, integrity of data and protection from replay. The security and efficiency being the basic parameters used to design a new sensor network protocol. A wireless sensor node integrates one or more sensors, …
ASSP Adaptive Self-dependent Security Protocol for
Reducing Radio Energy Consumption of Key Management
Security protocols in sensor networks hu-berlin.de
Routing Protocols in Wireless Sensor Networks – A Survey Shio Kumar Singh 1, M P Singh 2, Wireless Sensor Networks, Routing Protocols, Cluster Head 1. Introduction Wireless sensor network (WSN) is widely considered as one of the most important technologies for the twenty-first century [1]. In the past decades, it has received tremendous attention from both academia and industry all over
Spin protocols ppt Wireless Sensor Network Computer
SECURITY IN WIRELESS SENSOR NETWORKS A FORMAL
(PDF) SPINS Security Protocols for Sensor Networks
Abstract. Wireless sensor networks will be widely deployed in the near future. While much research has focused on making these networks feasible and useful, security has received little attention. We present a suite of security protocols optimized for sensor networks: SPINS. SPINS has two secure
SPINS Security Protocols for Sensor Networks SlideShare
SPINS Security Protocols for Sensor Networks Putra
ASSP Adaptive Self-dependent Security Protocol for
For example, SPINS [2] used RC5 [3] as the block cipher. TinySec [4] used Skipjack [5] as the default block cipher. Neighborhood Based Security Protocol is used to provide authentication in Wireless Sensor Network’s(WSN).NEKAP [6], a design of link layer key agreement protocol for sensor networks. NEKAP can provide the Confidentiality but sometimes this protocol fails to provide
PPT SPINS Security Protocols for Sensor Networks
“SPINS: Security protocols for sensor networks.” [ACM Journal of] Wireless Networks, 8:5, September 2002, pp. 521-534 Abstract Wireless sensor networks will be widely deployed in …
REVIEW ON SECURITY PROTOCOLS IN WIRELESS SENSOR NETWORKS
Automatic Security Protocol Generation and Verification. A First Step towards the Automatic Generation of Security Protocols PS, PS.GZ, PDF, HTML, BIB, with Dawn Song.
SPINS Security Protocols For Sensor Networks
On the Security of Cluster-based Communication Protocols
Seminar Topic: SPIN – Protocols for Wireless Sensor Networks Motivation • Dissemination is the process of distributing individual sensor observations to the whole network, treating all sensors as sink nodes • Limited supply of energy • Limited computational power • Limited communication resources
SPINS Security protocols for sensor networks Dhanraj
spins security protocols for sensor networks docx
Verifying Security Protocols for Sensor Networks Using
Automatic Security Protocol Generation and Verification. A First Step towards the Automatic Generation of Security Protocols PS, PS.GZ, PDF, HTML, BIB, with Dawn Song.
Security Protocols for Sensor Networks wmich.edu
SPINS Security Protocols for Sensor Networks ece.cmu.edu
SPINS Security Protocols for Sensor Networks People
Introduction Full paper: Postscript, PS.GZ, PDF. SPINS: Security Protocols for Sensor Networks. Adrian Perrig, Robert Szewczyk, Victor Wen, David Culler, J. D. Tygar
ASSP Adaptive Self-dependent Security Protocol for
KEY DISTRIBUTION AND DISTRIBUTED INTRUSION DETECTION
Introduction to Security Protocols for Sensor Network
Wireless Networks 8, 521–534, 2002 2002 Kluwer Academic Publishers. Manufactured in The Netherlands. SPINS: Security Protocols for Sensor Networks ADRIAN PERRIG, ROBERT…
Verifying Security Protocols for Sensor Networks Using
A Review of various security protocols in Wireless Sensor Network Anupma Sangwan1, Deepti Sindhu2, An ideal sensor network protocol should provide data authentication, confidentiality, integrity of data and protection from replay. The security and efficiency being the basic parameters used to design a new sensor network protocol. A wireless sensor node integrates one or more sensors, …
Light Weight Security Protocol for Wireless Sensor Network
The paper studies an authenticated routing pro- protocols in the sensor networks. tocol and a two-party key agreement protocol, and demonstrates that our security building blocks greatly facilitate the implementa- Communication architecture tion of a complete security solution for a sensor network. A common characteristic of sensor networks is their severely Generally, the sensor nodes
Energy efficient security protocols for wireless sensor
FORMAL ANALYSIS OF SECURITY PROTOCOLS FOR WIRELESS SENSOR NETWORKS node in the sequence. A length of a path is the number of edges in the path.
SPINS security protocols for sensor networks 10.1145
SPINS Security protocols for Sensor Networks Request PDF
spins security protocols for sensor networks docx
0 Votos desfavoráveis, marcar como não útil. SPINS: Security Protocols for Sensor Networks. Enviado por c4sudhir
KEY DISTRIBUTION AND DISTRIBUTED INTRUSION DETECTION
Security Analysis in Wireless Sensor Networks Murat
Abstract: In wireless sensor networks (WSNs), Security is critical for many sensor network applications, such as military target tracking and security monitoring. In particular, providing authentication to small sensor nodes is challenging, due to the limited capabilities of sensor …
Reducing Radio Energy Consumption of Key Management
Security in sensor networks is possible in a limited way, but it requires resources and generates overhead, which shortens the overall lifetime of the network. References Adrian Perrig, Robert Szewczyk, J.D. Tygar, Victor Wen, David E. Culler: SPINS – Security Protocols for Sensor Networks
Verifying Security Protocols for Sensor Networks Using
An Improved- SPIN Protocol for Wireless Sensor Networks
“SPINS: Security Protocols for Sensor Networks,” MobiCom 2001, pp.189-199, July 2001. 2 Outline Introduction SPINS Security Building Blocks Application Evaluation Conclusion. 3 Introduction (1/2) This paper presents a suite of security building blocks optimized for resource constrained environments and wireless communication. This approach is considered to be a master key theorem which
Verifying Security Protocols for Sensor Networks Using
sensor nodes in terms of energy, storage and computational ability, many security issues have arisen in such applications. As a result, many solutions and approaches have been proposed for …
SPINS Security Protocols for Sensor Networks CORE
LiSP A Lightweight Security Protocol for Wireless Sensor