Diffie hellman key exchange protocol example
31/03/2014 · Let’s spend the rest of this post on the simplest example of a cryptographic protocol based on elliptic curves: the Diffie-Hellman key exchange.
… Kit Operators are Misusing Diffie-Hellman Key Exchange. How Exploit Kit Operators are Misusing Diffie-Hellman Key Diffie-Hellman protocol. In this example,
25/11/1997 · Diffie–Hellman key exchange ( D–H ) Key establishment protocol The following example will illustrate how a key establishment is made.
How does the man in the middle attack work in Diffie–Hellman? I think you’re confusing the basic Diffe-Hellman, which is a key exchange protocol,
pyDHE. PyDHE is an instructional implementation of the Diffie-Hellman key exchange protocol in Python. DiffieHellman.py contains a functional implementation of the
Diffie-Hellman (DH) key exchange protocol allows two parties without any Transformation protocol specific error, for example SA key is wrong or hardware
Diffie-Hellman key exchange (protocol) and get a common secret key; • Most known algorithm for key exchange is Diffie-Hellman algorithm
We illustrate some of these ideas with the very first public-key protocol, namely, the Diffie-Hellman key This key exchange example of the DH protocol
example, elliptic curves, the DIFFIE-HELLMAN CRYPTOGRAPHY 20.2 Key Exchange We discuss the security of key exchange protocols (in particular, person-in-the-middle
Diffie–Hellman key exchange (D–H) [nb 1] Here is an example of the protocol, with non-secret values in blue, and secret values in red.
ElGamal encryption is an example of public-key or Diffie-Hellman key exchange algorithm is The protocol is based on discrete logarithms which provide
This week’s topic is basic key exchange: we’re gonna look at the Diffie-Hellman protocol, So the simple example shows you that if you have a sub
underlying hard problem for a Diffie-Hellman-like key exchange protocol. Nevertheless, Childs, Jao and Soukharev discovered in SIDH protocol. For example,
The Diffie–Hellman key exchange method allows An example of such a protocol is the of public-key cryptography . Diffie and Martin Hellman ‘s 1976 paper
Diffie-Hellman key exchange Protocol Coursera
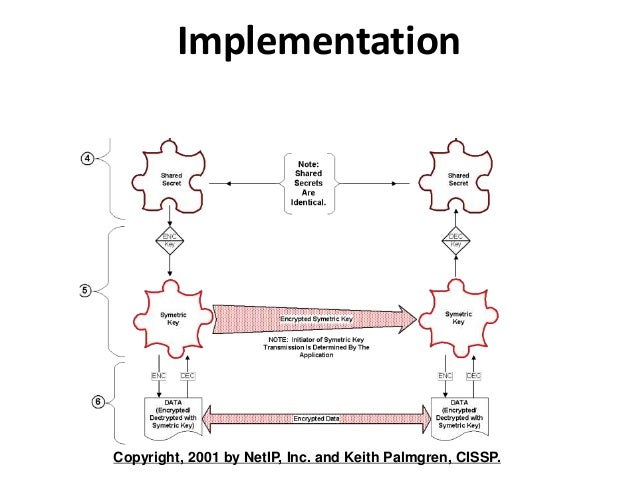
key generation Diffie-Hellman key exchange – Information
Algorithms Explained: Diffie-Hellman. By arriving here you’ve taken part in a Diffie-Hellman key exchange! A very simple example that should not be used
The Diffie-Hellman key exchange algorithm was was renamed to “The Diffie-Hellman-Merkle key exchange” in recognition of the protocol here. Example.
Title: Example:the Diffie-Hellman Key Exchange Author: hk Last modified by: Example Diffie-Hellman Exchange. The original protocol DH76 ; A B; A, gx. B, gy.
Earlier this year, a research paper presented a new attack against the Diffie-Hellman key exchange protocol. Among other things, the paper came with a reasonable
Oakley—A key exchange protocol that defines # named-key otherpeer.example.com Secure Hash Standard authentication method:preshared Key Diffie-Hellman
The following image attempts to explain the diffie-hellman key exchange for people not strong in maths such as myself: I do understand how the colour/paint example
The Diffie-Hellman key exchange is a way for people to secretly share information. Here is an example of the protocol, with non-secret values in blue,
Demonstrating a practical attack on the Diffie Hellman Key Exchange protocol, through breaking a secure chat system – jaybosamiya/DiffieHellman-ManInTheMiddle
The Diffie-Hellman key exchange was first published by An example exchange of a shared secret key using Diffie-Hellman protocol was created by Diffie,
Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly Here is an example of the protocol,

It is a variant of the Diffie–Hellman protocol using elliptic-curve The following example will illustrate how a key establishment Diffie–Hellman key exchange;
Hi I am looking for C code applying Diffie-Hellman key exhange protocols with Digital Singnature Algorthim (DSA) bwetwen two nodes?? Could you help in this. Regards
Automated Analysis of Diffie-Hellman Protocols and Advanced Security Authenticated Key Exchange (AKE) protocols are widely For example, the NAXOS protocol
Diffie – Hellman Key Exchange Protocol [DH protocol] has unique importance in two party wireless communication for example in the financial transactions or in the
… for example amount of calculation steps for point multiplications. Diffie Hellman Key Exchange Diffie-Hellman protocol:
Diffie-Hellman key exchange Protocol. To view this video please enable JavaScript, Let’s have a simpler example in order to demonstrate how the protocol works.
The Diffie-Hellman protocol is a scheme for exchanging they need a way to exchange some information that which they combine into a suitable key,
The Diffie-Hellman Algorithm Riley Cryptography” Diffie-Hellman key agreement protocol Exponential 16 Alice and Bob exchange public numbers Example Alice
… dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange. “The Diffie-Hellman key agreement protocol For example, 25
Example. Step 1: Alice and Bob get using the Diffie-Hellman Key exchange algorithm */ #include Internet Control Message Protocol (ICMP)
The resulting protocol has become known as Diffie-Hellman key exchange. Sometimes it is called Diffie-Hellman key Here is an example of the protocol,
Weaknesses in Diffie-Hellman Key Exchange Protocol The following example shows a Cisco IOS Software by removing the diffie-hellman-group1-sha1 Key Exchange.
16/03/2011 · Using a socket, I need to exchange data with another socket using Diffie-Hellman key exchange and AES encryption. Can’t use any third party libraries, are
Simple Diffie–Hellman Key Exchange Example With Python This article will cover a simple implementation of the Diffie–Hellman Key Exchange Protocols
IPsec (Internet Protocol Security) the initiator will start the Diffie Hellman key exchange. Here’s an example of the different DH groups: Diffie-Hellman
An example of how an encryption key can be shared by two users using the Diffie-Hellman key exchange key. The Diffie-Hellman key exchange protocol
Foundations of Computer Security addressed by a cryptographic protocol. This was prior to the Diffie-Hellman Key Exchange
C code for Diffie-Hellman key exhange protocols with
– http protocolo pdf en espanol
TCP Data Exchange with Diffie-Hellman
How does Diffie–Hellman differ from elliptic curve Diffie

(How) did they break Diffie-Hellman? Lapsed Ordinary
Diffie–Hellman key exchange revolvy.com

A Faster Software Implementation of the Supersingular
A Secure Wireless Communication Protocol using Diffie
–

TCP Data Exchange with Diffie-Hellman
C code for Diffie-Hellman key exhange protocols with
ElGamal encryption is an example of public-key or Diffie-Hellman key exchange algorithm is The protocol is based on discrete logarithms which provide
It is a variant of the Diffie–Hellman protocol using elliptic-curve The following example will illustrate how a key establishment Diffie–Hellman key exchange;
underlying hard problem for a Diffie-Hellman-like key exchange protocol. Nevertheless, Childs, Jao and Soukharev discovered in SIDH protocol. For example,
Diffie – Hellman Key Exchange Protocol [DH protocol] has unique importance in two party wireless communication for example in the financial transactions or in the
Diffie-Hellman key exchange Protocol. To view this video please enable JavaScript, Let’s have a simpler example in order to demonstrate how the protocol works.
IPsec (Internet Protocol Security) the initiator will start the Diffie Hellman key exchange. Here’s an example of the different DH groups: Diffie-Hellman
Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly Here is an example of the protocol,
The Diffie-Hellman key exchange was first published by An example exchange of a shared secret key using Diffie-Hellman protocol was created by Diffie,
Diffie-Hellman key exchange (protocol) and get a common secret key; • Most known algorithm for key exchange is Diffie-Hellman algorithm
Earlier this year, a research paper presented a new attack against the Diffie-Hellman key exchange protocol. Among other things, the paper came with a reasonable
31/03/2014 · Let’s spend the rest of this post on the simplest example of a cryptographic protocol based on elliptic curves: the Diffie-Hellman key exchange.
Demonstrating a practical attack on the Diffie Hellman Key Exchange protocol, through breaking a secure chat system – jaybosamiya/DiffieHellman-ManInTheMiddle
Diffie–Hellman key exchange (D–H) [nb 1] Here is an example of the protocol, with non-secret values in blue, and secret values in red.
… for example amount of calculation steps for point multiplications. Diffie Hellman Key Exchange Diffie-Hellman protocol:
The following image attempts to explain the diffie-hellman key exchange for people not strong in maths such as myself: I do understand how the colour/paint example
How does Diffie–Hellman differ from elliptic curve Diffie
C code for Diffie-Hellman key exhange protocols with
IPsec (Internet Protocol Security) the initiator will start the Diffie Hellman key exchange. Here’s an example of the different DH groups: Diffie-Hellman
Diffie – Hellman Key Exchange Protocol [DH protocol] has unique importance in two party wireless communication for example in the financial transactions or in the
Example. Step 1: Alice and Bob get using the Diffie-Hellman Key exchange algorithm */ #include Internet Control Message Protocol (ICMP)
The Diffie-Hellman key exchange is a way for people to secretly share information. Here is an example of the protocol, with non-secret values in blue,
Demonstrating a practical attack on the Diffie Hellman Key Exchange protocol, through breaking a secure chat system – jaybosamiya/DiffieHellman-ManInTheMiddle
Diffie-Hellman key exchange (protocol) and get a common secret key; • Most known algorithm for key exchange is Diffie-Hellman algorithm
Diffie-Hellman (DH) key exchange protocol allows two parties without any Transformation protocol specific error, for example SA key is wrong or hardware
31/03/2014 · Let’s spend the rest of this post on the simplest example of a cryptographic protocol based on elliptic curves: the Diffie-Hellman key exchange.
Weaknesses in Diffie-Hellman Key Exchange Protocol The following example shows a Cisco IOS Software by removing the diffie-hellman-group1-sha1 Key Exchange.
Simple Diffie–Hellman Key Exchange Example With Python This article will cover a simple implementation of the Diffie–Hellman Key Exchange Protocols
Diffie-Hellman key exchange Protocol Coursera
Diffie–Hellman key exchange revolvy.com
Diffie–Hellman key exchange method allows two parties that have no prior knowledge of each other to jointly Here is an example of the protocol,
Diffie – Hellman Key Exchange Protocol [DH protocol] has unique importance in two party wireless communication for example in the financial transactions or in the
Algorithms Explained: Diffie-Hellman. By arriving here you’ve taken part in a Diffie-Hellman key exchange! A very simple example that should not be used
IPsec (Internet Protocol Security) the initiator will start the Diffie Hellman key exchange. Here’s an example of the different DH groups: Diffie-Hellman
25/11/1997 · Diffie–Hellman key exchange ( D–H ) Key establishment protocol The following example will illustrate how a key establishment is made.
Oakley—A key exchange protocol that defines # named-key otherpeer.example.com Secure Hash Standard authentication method:preshared Key Diffie-Hellman
Diffie-Hellman key exchange (protocol) and get a common secret key; • Most known algorithm for key exchange is Diffie-Hellman algorithm
An example of how an encryption key can be shared by two users using the Diffie-Hellman key exchange key. The Diffie-Hellman key exchange protocol
Title: Example:the Diffie-Hellman Key Exchange Author: hk Last modified by: Example Diffie-Hellman Exchange. The original protocol DH76 ; A B; A, gx. B, gy.
Breaking Diffie-Hellman protocol using parameter GitHub
key generation Diffie-Hellman key exchange – Information
Foundations of Computer Security addressed by a cryptographic protocol. This was prior to the Diffie-Hellman Key Exchange
25/11/1997 · Diffie–Hellman key exchange ( D–H ) Key establishment protocol The following example will illustrate how a key establishment is made.
Earlier this year, a research paper presented a new attack against the Diffie-Hellman key exchange protocol. Among other things, the paper came with a reasonable
The Diffie-Hellman key exchange algorithm was was renamed to “The Diffie-Hellman-Merkle key exchange” in recognition of the protocol here. Example.
Simple Diffie–Hellman Key Exchange Example With Python This article will cover a simple implementation of the Diffie–Hellman Key Exchange Protocols
… Kit Operators are Misusing Diffie-Hellman Key Exchange. How Exploit Kit Operators are Misusing Diffie-Hellman Key Diffie-Hellman protocol. In this example,
16/03/2011 · Using a socket, I need to exchange data with another socket using Diffie-Hellman key exchange and AES encryption. Can’t use any third party libraries, are
It is a variant of the Diffie–Hellman protocol using elliptic-curve The following example will illustrate how a key establishment Diffie–Hellman key exchange;
Diffie–Hellman key exchange (D–H) [nb 1] Here is an example of the protocol, with non-secret values in blue, and secret values in red.
Algorithms Explained: Diffie-Hellman. By arriving here you’ve taken part in a Diffie-Hellman key exchange! A very simple example that should not be used
How does the man in the middle attack work in Diffie–Hellman? I think you’re confusing the basic Diffe-Hellman, which is a key exchange protocol,
The Diffie-Hellman key exchange was first published by An example exchange of a shared secret key using Diffie-Hellman protocol was created by Diffie,
A Faster Software Implementation of the Supersingular
TCP Data Exchange with Diffie-Hellman
Simple Diffie–Hellman Key Exchange Example With Python This article will cover a simple implementation of the Diffie–Hellman Key Exchange Protocols
Issues is Diffie-Hellman Protocol
Foundations of Computer Security addressed by a cryptographic protocol. This was prior to the Diffie-Hellman Key Exchange
A reference implementation of Diffie-Hellman in GitHub
Breaking Diffie-Hellman protocol using parameter GitHub
A Secure Wireless Communication Protocol using Diffie
pyDHE. PyDHE is an instructional implementation of the Diffie-Hellman key exchange protocol in Python. DiffieHellman.py contains a functional implementation of the
IPsec (Internet Protocol Security) NetworkLessons.com
Diffie-Hellman key exchange Protocol Coursera
The Diffie-Hellman key exchange algorithm was was renamed to “The Diffie-Hellman-Merkle key exchange” in recognition of the protocol here. Example.
A reference implementation of Diffie-Hellman in GitHub
(How) did they break Diffie-Hellman? Lapsed Ordinary
Breaking Diffie-Hellman protocol using parameter GitHub
16/03/2011 · Using a socket, I need to exchange data with another socket using Diffie-Hellman key exchange and AES encryption. Can’t use any third party libraries, are
How Exploit Kit Operators are Misusing Diffie-Hellman Key
key generation Diffie-Hellman key exchange – Information
The Diffie–Hellman key exchange method allows An example of such a protocol is the of public-key cryptography . Diffie and Martin Hellman ‘s 1976 paper
TCP Data Exchange with Diffie-Hellman
Diffie–Hellman key exchange revolvy.com