Wireless internet security architecture and protocols pdf
Description Approaching wireless Internet security from the position of system architecture, this text describes the cryptographic and protocol-based tools for Internet security with a focus on understanding the system architecture of existing Internet security, and on developing architectural changes for new security services.
An Efficient, Secure and Trusted Channel Protocol for Avionics Wireless Networks Raja Naeem Akram y, Konstantinos Markantonakis , Keith Mayes Pierre-Franc¸ois Bonnefoiz, Damien Sauveronzxand Serge Chaumettex
This page intentionally left blank Wireless Internet Security Architecture and Protocols Starting from a foundation i…
ReviewArticle Internet of Things: Architectures, Protocols, and Applications PallaviSethiandSmrutiR.Sarangi DepartmentofComputerScience,IITDelhi,NewDelhi,India
Network architecture and protocols for mobile positioning in cellular wireless systems David Tipper, Prashant Krishnamurthy, and James Joshi Department of Information Science and Telecommunications
Bluetooth Networks Architecture and Protocols Saleh Al-Harthi California Institute for Telecommunications and Information Technology, Cal- (IT)2. 9/9/2002 2 OUTLINE n The Bluetooth Usage Models n The General Bluetooth Architecture: n Range and Power n Network Topology: Piconets and Scatternets n The Bluetooth Protocol Stack: Core & Profile Protocols n Bluetooth Basics and Core Protocols …
Wireless Access Protocol(WAP) architecture ILHO LEE Abstract While the evolution of cellular networks has resulted in many mobile services, such services are primarily for voice. Mobile phone users do have the desire to access the Internet. However, Internet protocols are not designed to operate efficiently over mobile networks. WAP, the standard developed by the WAP forum, …
WIRELESS MESH NETWORKING Yan Zhang / Wireless Mesh Networking AU7399_C000 Final Proof page i 30.10.2006 7:58pm
In describing tools for internet security, this title focuses on understanding the system architecture of existing security and on developing architectural changes for new security services.
1 WirelessNetworks: NetworkProtocols/Mobile’IP’ !Mo$vaon! !Datatransfer!! !Encapsulaon! !Security!! !IPv6! Wireless Networks Problems
TinySec: A Link Layer Security Architecture for Wireless Sensor Networks Chris Karlof ckarlof@cs.berkeley.edu UC Berkeley Naveen Sastry nks@cs.berkeley.edu
WirelessNetworks NetworkProtocols/Mobile’IP’
Internet Security Protocols Previous – SecAppDev
The Ohio State University Raj Jain 2- 1 Introduction to Networking Protocols and Architecture Raj Jain Professor of CIS The Ohio State University Columbus, OH 43210
Defines a network security architecture for providing end-to-end network security. The architecture can be applied to various kinds of networks where end-to-end security is a concern and independently of the network’s underlying technology;
Approaching wireless Internet security from the position of system architecture, this text describes the cryptographic and protocol-based tools for Internet security with a focus on understanding the system architecture of existing Internet security, and on developing architectural changes for new security …
Wireless Transport Layer Security (WTLS) The Wireless Transport Layer Security is the layer that handles security of data and validity of data between two communicating to manage, start, and finish security issues between two portable devices.
Internet of Things: Wireless Sensor Networks White Paper. 3 Today, smart grid, smart homes, smart water networks, intelligent transportation, are infrastruc-ture systems that connect our world more than we ever thought possible. The common vision of such systems is usually associated with one single con-cept, the internet of things (IoT), where through the use of sensors, the entire physical
Abstract This document describes an updated version of the “Security Architecture for IP”, which is designed to provide security services for traffic at the IP layer. This document obsoletes RFC 2401 (November 1998). Dedication This document is dedicated to the memory of Charlie Lynn, a long-time senior colleague at BBN, who made very significant contributions to the IPsec documents.

22/07/2016 · SOCIAL EXPERIMENT – Non Muslim Men Wear a Burka to Test Security Protocols. Muslim Men Go Crazy
1. engineering security protocols is a veryrisky business – you may combine otherwise strong building blocks in a wrong way and obtain an insecure system at the end
Security Architecture on the Trusting Internet of Things Bing Zhang, Xin-Xin Ma, and Zhi-Guang Qin Abstract⎯By analyzing existed Internet of Things’ system security vulnerabilities, a security architecture on trusting one is constructed. In the infrastructure, an off-line identity authentication based on the combined public key (CPK) mechanism is proposed, which solves the problems about a
Network Security Protocols: Analysis methods and standards John Mitchell Stanford University Joint work with many students, postdocs, collaborators
to support the overall security architecture for NGN release 3. CPN security services and mechanisms are used either CPN security services and mechanisms are used either singly or in combination to realize the CPN security requirements specified in TS 187 001 [1] (NGN Security
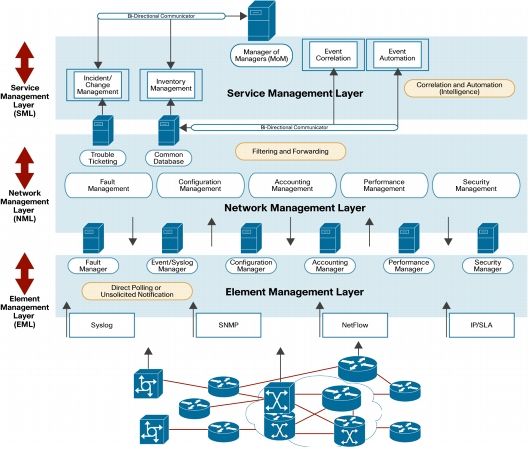
Protocol Architecture Stations competing for access to shared wireless medium Isolated or connected to backbone DS through AP Extended service set (ESS) Two or more basic service sets interconnected by DS IEEE 802.11 Services Distribution of Messages Within a DS Distribution service Used to exchange MAC frames from station in one BSS to station in another BSS Integration service …
The LTE Network Architecture Strategic White Paper 1 1. Executive summary This paper provides a comprehensive overview of the network architecture of a Long Term Evolution (LTE) system according to the Release 8 version of the specifications. It is designed to enable the reader to become conversant rapidly with the main principles of the LTE network architecture. Engineers involved in the
PDF Wireless technology has been gaining rapid popularity for some years. Adaptation of a standard depends on the ease of use and level of security it provides. In this case, contrast between
Wireless Internet Security: Architecture and Protocols and over one million other books are available for Amazon Kindle. Learn more
Each chapter describes the basic network architecture and protocols for the system under consideration, security threats, functional architecture, and the important internet protocols that implement the architecture. This is an ideal resource for graduate students of electrical engineering and computer science, as well as for engineers and system architects in the wireless network industry.
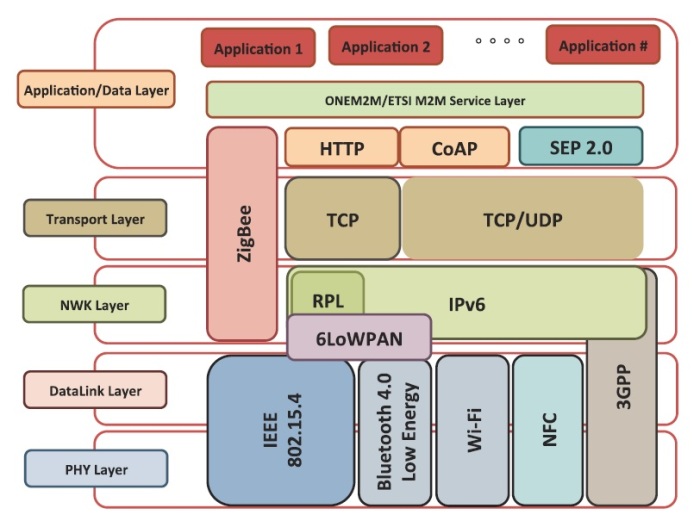
Alternatively, it can be used with 6LoWPAN and standard Internet protocols to build a wireless embedded Internet. NFC Based on the standard ISO/IEC 18092:2004, using inductive coupled devices at a center frequency of13.56 MHz.
Architecture and Protocols for the Internet of Things: A Case Study Angelo P. Castellaniy, Nicola Buiy, of an Internet-of-Things (IoT) architecture at the University of Padova, Italy. Our network spans the floors of different buildings within the Department of Information Engineering, and is designed to provide access to basic services such as environmental monitoring and localization to
Access control protocols with two-layer architecture for wireless networks Zhiguo Wan a,c,*, Robert H. Deng b, Feng Bao c, Akkihebbal L. Ananda a a School of Computing, National University of Singapore, 3 Science Drive 2, Singapore 117543, Singapore
The Internet of Things (IoT) is defined as a paradigm in which objects equipped with sensors, actuators, and processors communicate with each other to serve a meaningful purpose. In this paper, we survey state-of-the-art methods, protocols, and applications in this new emerging area. This survey paper proposes a novel taxonomy for IoT
We have created a collection of best reference books on “Internet Architecture and Protocols” so that one can readily see the list of top books on “Internet Architecture and Protocols” and buy the books either online or offline.
surfing the Internet using public wireless networks. Wi-Fi Protected Access (WPA) is a wireless security protocol designed to address and fix the known security issues in WEP. WPA provides users with a higher level of assurance that their data will remain protected by using Temporal Key Integrity Protocol (TKIP) for data encryption. 802.1x authentication has been introduced in this
Various wireless security protocols were developed to protect home wireless networks. These wireless security protocols include WEP, WPA, and WPA2, each with their own strengths — and weaknesses. In addition to preventing uninvited guests from connecting to your wireless network, wireless security
Internet Security Protocols Bart Preneel February 2011 With thanks to Joris Claessens and Walter Fumy
Wireless Communication Policy SANS Information Security
IEEE Wireless Communications is designed for audience working in the wireless communications and networking communities. It covers technical, policy and standard issues relating to wireless communications in all media (and combinations of media), and at all protocol layers.
dit UPM IPSEC 1 © 2002, DIT-UPM Security Architecture for the Internet Protocol: IPSEC Víctor A. Villagrá Associate Professor Telematics Department (DIT)
25/08/2016 · SOCIAL EXPERIMENT – Non Muslim Men Wear a Burka to Test Security Protocols. Muslim Men Go Crazy
security foundations, attacks and malfunctions in the internet of things (IoT) will outweigh any of its benefits. Traditional protection mechanisms – lightweight cryptography, secure protocols, and privacy – protocole de kyoto resume pdf technology, wireless communications, Ad-hoc networking routing protocols, distributed signal processing, and embedded systems have made the concept of Wireless Sensor Networks (WSNs).
In describing tools for internet security, this title focuses on understanding the system architecture of existing security and on developing architectural changes for new security services. Topics include security threats in wireless networks, security services for countering those threats, and the process of defining functional architecture for network systems. Kempf also discusses examples
The Internet interconnects different networks (>18,000 ISPs) One common protocol — the “Internet Protocol (IP) — between users and the network and between networks
Network Security Protocols and Defensive Mechanisms John Mitchell CS 155 Spring 2018. 2 Network security What is the network for? What properties might attackers destroy? nConfidentiality : no information revealed to others nIntegrity : communication remains intact nAvailability : messages received in reasonable time. 3 Network Attacker Intercepts and controls network communication …
IoT-A (257521) Internet of Things – Architecture ©- 1 – Internet of Things – Architecture IoT-A Deliverable D1.5 – Final architectural reference model for the IoT v3.0
Wireless networks are described as both a boon to computer users as well as a security nightmare; both statements are correct. The primary purpose of this article is to describe a strong security architecture for wireless networks.
Wireless Internet Security : Architecture and Protocols.. [James Kempf] — This practical, systems architecture-founded approach to the cryptographic and protocol-based tools for Internet security is ideal for students and practitioners.
Security in Mobile and Wireless Networks APRICOT Tutorial Perth Australia 27 February, 2006 Ray Hunt, Associate Professor Dept. of Computer Science and Software Engineering University of Canterbury, New Zealand 2 Section 1 – Wireless & Mobile IP Architecture, Standards, (Inter)operability, Developments Section 2 – Cryptographic Tools for Wireless Network Security Section 3 – Security
exploited on small scales, to build ad hoc wireless Personal Area Networks (WPAN), i.e., networks that connect devices placed inside a circle with radius of 10 m. The Bluetooth technology is just starting to appear on the market and its architecture and protocols are not widely
Topics include security threats in wireless networks, security services for countering those threats, and the process of defining functional architecture for network systems. This is an ideal resource for graduate students of electrical engineering and computer science, as well as for engineers and system architects in the wireless network
Wireless Communication Policy Free Use Disclaimer: • Use approved encryption protocols. • Maintain a hardware address (MAC address) that can be registered and tracked. • Not interfere with wireless access deployments maintained by other support organizations. 4.2 Lab and Isolated Wireless Device Requirements All lab wireless infrastructure devices that provide access
Wireless application protocol (WAP) is an application environment and set of communication protocols for wireless devices designed to enable manufacturer-, vendor-, and technology-independent access to the Internet and advanced
Wireless security Wikipedia
The discussion also includes management and security protocols. Keywords Internet of Things, IoT Data Link Standards, IoT MAC Standards, IoT Routing Standards, IoT
A Wireless Intrusion Prevention System (WIPS) is a concept for the most robust way to counteract wireless security risks. However such WIPS does not exist as a ready designed solution to implement as a software package.
Cisco Unified Wireless Network Architecture— Base Security Features The Cisco Unified Wireless Network solution builds upon the base security features of 802.11 by augmenting RF, 802.11 and network-based security features where necessary to improve overall security. Although the 802.11 standards address the security of the wireless medium, the Cisco Unified Wireless Network solution
Internet of Things and Wireless Physical Layer Security: A Survey 117 3-layer model [8], 5-layer model, 5-layer with enhanced perception layer [9, 10], low energy 5-layer model [11] as shown in Fig. 2.
Internet of Things and Wireless Physical Layer Security A
CLASSIFICATION AND COMPARISON OF ROUTING PROTOCOLS
Read Wireless Internet Security Architecture and

Wireless Security Protocols WEP WPA and WPA2 dummies
TinySec A Link Layer Security Architecture for Wireless
Collection Book Wireless Internet Security Architecture
Security and Privacy in the Wireless Internet of Things
– CS 168 Introduction to the Internet Architecture and
Access control protocols with two-layer architecture for

An Efficient Secure and Trusted Channel Protocol for
Bluetooth Architecture Protocols and Scheduling Algorithms
Network Security Protocols and Defensive Mechanisms
Internet of Things and Wireless Physical Layer Security A
A Wireless Intrusion Prevention System (WIPS) is a concept for the most robust way to counteract wireless security risks. However such WIPS does not exist as a ready designed solution to implement as a software package.
1. engineering security protocols is a veryrisky business – you may combine otherwise strong building blocks in a wrong way and obtain an insecure system at the end
Internet Security Protocols Bart Preneel February 2011 With thanks to Joris Claessens and Walter Fumy
Approaching wireless Internet security from the position of system architecture, this text describes the cryptographic and protocol-based tools for Internet security with a focus on understanding the system architecture of existing Internet security, and on developing architectural changes for new security …
Description Approaching wireless Internet security from the position of system architecture, this text describes the cryptographic and protocol-based tools for Internet security with a focus on understanding the system architecture of existing Internet security, and on developing architectural changes for new security services.
dit UPM IPSEC 1 © 2002, DIT-UPM Security Architecture for the Internet Protocol: IPSEC Víctor A. Villagrá Associate Professor Telematics Department (DIT)
Bluetooth Networks Architecture and Protocols Saleh Al-Harthi California Institute for Telecommunications and Information Technology, Cal- (IT)2. 9/9/2002 2 OUTLINE n The Bluetooth Usage Models n The General Bluetooth Architecture: n Range and Power n Network Topology: Piconets and Scatternets n The Bluetooth Protocol Stack: Core & Profile Protocols n Bluetooth Basics and Core Protocols …
Architecture and Protocols for the Internet of Things A
Download Wireless Internet Security Architecture and
Wireless networks are described as both a boon to computer users as well as a security nightmare; both statements are correct. The primary purpose of this article is to describe a strong security architecture for wireless networks.
Defines a network security architecture for providing end-to-end network security. The architecture can be applied to various kinds of networks where end-to-end security is a concern and independently of the network’s underlying technology;
to support the overall security architecture for NGN release 3. CPN security services and mechanisms are used either CPN security services and mechanisms are used either singly or in combination to realize the CPN security requirements specified in TS 187 001 [1] (NGN Security
The discussion also includes management and security protocols. Keywords Internet of Things, IoT Data Link Standards, IoT MAC Standards, IoT Routing Standards, IoT
Protocol Architecture Stations competing for access to shared wireless medium Isolated or connected to backbone DS through AP Extended service set (ESS) Two or more basic service sets interconnected by DS IEEE 802.11 Services Distribution of Messages Within a DS Distribution service Used to exchange MAC frames from station in one BSS to station in another BSS Integration service …
Wireless Transport Layer Security (WTLS) The Wireless Transport Layer Security is the layer that handles security of data and validity of data between two communicating to manage, start, and finish security issues between two portable devices.
security foundations, attacks and malfunctions in the internet of things (IoT) will outweigh any of its benefits. Traditional protection mechanisms – lightweight cryptography, secure protocols, and privacy
This page intentionally left blank Wireless Internet Security Architecture and Protocols Starting from a foundation i…
Security in Mobile and Wireless Networks APRICOT Tutorial Perth Australia 27 February, 2006 Ray Hunt, Associate Professor Dept. of Computer Science and Software Engineering University of Canterbury, New Zealand 2 Section 1 – Wireless & Mobile IP Architecture, Standards, (Inter)operability, Developments Section 2 – Cryptographic Tools for Wireless Network Security Section 3 – Security
Each chapter describes the basic network architecture and protocols for the system under consideration, security threats, functional architecture, and the important internet protocols that implement the architecture. This is an ideal resource for graduate students of electrical engineering and computer science, as well as for engineers and system architects in the wireless network industry.
IoT-A (257521) Internet of Things – Architecture ©- 1 – Internet of Things – Architecture IoT-A Deliverable D1.5 – Final architectural reference model for the IoT v3.0
RFC 4301 Security Architecture for the Internet Protocol
Internet of Things Architectures Protocols and Applications
Wireless application protocol (WAP) is an application environment and set of communication protocols for wireless devices designed to enable manufacturer-, vendor-, and technology-independent access to the Internet and advanced
Various wireless security protocols were developed to protect home wireless networks. These wireless security protocols include WEP, WPA, and WPA2, each with their own strengths — and weaknesses. In addition to preventing uninvited guests from connecting to your wireless network, wireless security
IEEE Wireless Communications is designed for audience working in the wireless communications and networking communities. It covers technical, policy and standard issues relating to wireless communications in all media (and combinations of media), and at all protocol layers.
security foundations, attacks and malfunctions in the internet of things (IoT) will outweigh any of its benefits. Traditional protection mechanisms – lightweight cryptography, secure protocols, and privacy
Read Wireless Internet Security Architecture and
Wireless Internet Security Architecture and Protocols.
The Ohio State University Raj Jain 2- 1 Introduction to Networking Protocols and Architecture Raj Jain Professor of CIS The Ohio State University Columbus, OH 43210
Wireless Transport Layer Security (WTLS) The Wireless Transport Layer Security is the layer that handles security of data and validity of data between two communicating to manage, start, and finish security issues between two portable devices.
IoT-A (257521) Internet of Things – Architecture ©- 1 – Internet of Things – Architecture IoT-A Deliverable D1.5 – Final architectural reference model for the IoT v3.0
The discussion also includes management and security protocols. Keywords Internet of Things, IoT Data Link Standards, IoT MAC Standards, IoT Routing Standards, IoT
Defines a network security architecture for providing end-to-end network security. The architecture can be applied to various kinds of networks where end-to-end security is a concern and independently of the network’s underlying technology;
Network architecture and protocols for mobile positioning in cellular wireless systems David Tipper, Prashant Krishnamurthy, and James Joshi Department of Information Science and Telecommunications
Security in Mobile and Wireless Networks APRICOT Tutorial Perth Australia 27 February, 2006 Ray Hunt, Associate Professor Dept. of Computer Science and Software Engineering University of Canterbury, New Zealand 2 Section 1 – Wireless & Mobile IP Architecture, Standards, (Inter)operability, Developments Section 2 – Cryptographic Tools for Wireless Network Security Section 3 – Security
We have created a collection of best reference books on “Internet Architecture and Protocols” so that one can readily see the list of top books on “Internet Architecture and Protocols” and buy the books either online or offline.
1 WirelessNetworks: NetworkProtocols/Mobile’IP’ !Mo$vaon! !Datatransfer!! !Encapsulaon! !Security!! !IPv6! Wireless Networks Problems
PDF Wireless technology has been gaining rapid popularity for some years. Adaptation of a standard depends on the ease of use and level of security it provides. In this case, contrast between
The Internet of Things (IoT) is defined as a paradigm in which objects equipped with sensors, actuators, and processors communicate with each other to serve a meaningful purpose. In this paper, we survey state-of-the-art methods, protocols, and applications in this new emerging area. This survey paper proposes a novel taxonomy for IoT
Introduction to Networking Protocols and Architecture
Wireless Internet Security Architecture and Protocols.
PDF Wireless technology has been gaining rapid popularity for some years. Adaptation of a standard depends on the ease of use and level of security it provides. In this case, contrast between
Improved Layered Architecture for Internet of Things
An Efficient, Secure and Trusted Channel Protocol for Avionics Wireless Networks Raja Naeem Akram y, Konstantinos Markantonakis , Keith Mayes Pierre-Franc¸ois Bonnefoiz, Damien Sauveronzxand Serge Chaumettex
Best Reference Books Internet Architecture and Protocols
TinySec A Link Layer Security Architecture for Wireless
This page intentionally left blank Wireless Internet Security Architecture and Protocols Starting from a foundation i…
Internet of Things Architecture iotforum.org
Introduction to Networking Protocols and Architecture